Security Operations Centers (SOCs) face an overwhelming volume of threat alerts, making it difficult to separate real threats from false positives without heavy resource use.
For teams already working with, or planning to adopt Filigran’s OpenCTI, ANY.RUN now offers powerful interoperability that bring real-time malware analysis and fresh threat intelligence directly into your existing workflows. This helps SOCs boost efficiency, cut response times, and act with confidence, all without replacing current tools.
Build Faster Response in OpenCTI with ANY.RUN
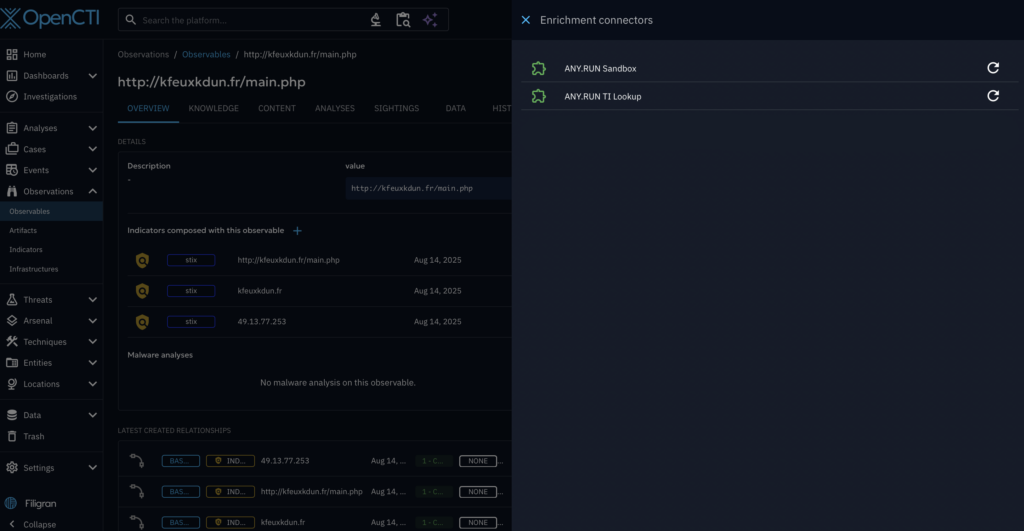
ANY.RUN now offers dedicated OpenCTI connectors for its main products, allowing SOC teams to use them with their existing security stack seamlessly. This means there is no need to change existing processes and tools, making interoperability simple for those already using OpenCTI.
Available for ANY.RUN’s Enterprise plan users, it is designed to improve SOC metrics for incident detection and response, streamline routine tasks, reduce response times, and provide deep analytics.
- Interactive Sandbox: Automate analysis of suspicious files and URLs to quickly understand their threat level, TTPs, and collect IOCs.
- Threat Intelligence Lookup: Enrich observables with threat context based on fresh live attack data.
- Threat Intelligence Feeds: Stay updated on the active threats with filtered, actionable network IOCs from the latest malware samples.
You can connect any combination of these connectors based on their specific needs and licenses.
View documentation on GitHub →
This connectors ensure that accurate threat info is accessible in just a few clicks, significantly boosting SOC effectiveness.
Automate Threat Analysis for Early Detection with Interactive Sandbox
ANY.RUN’s Interactive Sandbox is a cloud-based service that provides SOC teams with instant access to fully interactive Windows, Linux, and Android virtual machines for analyzing suspicious files and URLs.
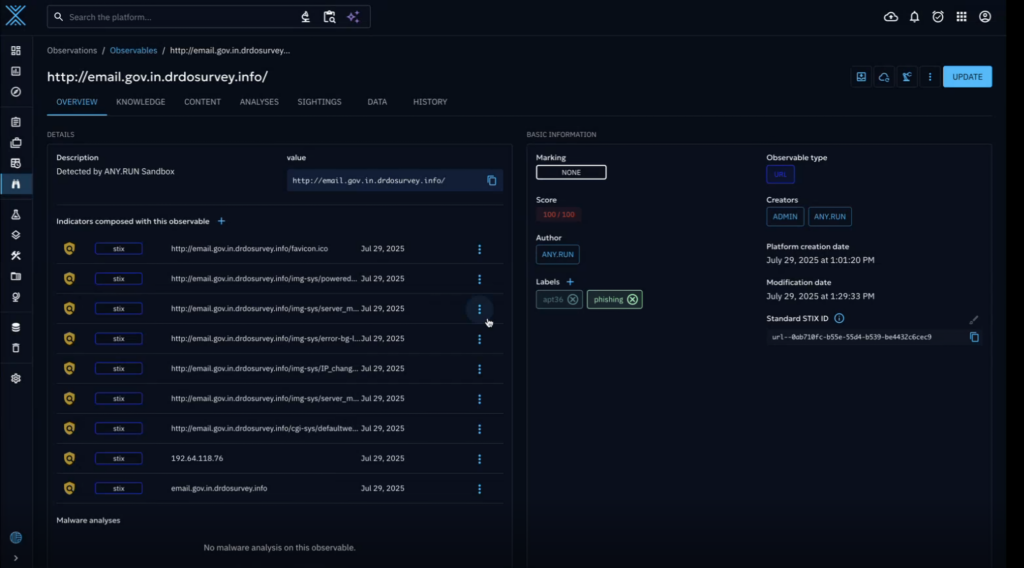
With the OpenCTI connector, SOC teams can:
- Send files or URLs directly from OpenCTI for instant analysis in ANY.RUN’s Interactive Sandbox.
- Automate the execution of multi-stage attacks to reach the final stage of an attack.
- Enrich observables in OpenCTI with indicators obtained from the sandbox analysis.
Use documentation to set up the connector →
The connector leverages the Automated Interactivity feature. It allows for automated execution of user actions like archive extraction, CAPTCHA solution, and payload launching to trigger each stage of an attack and ensure complete detection of the most evasive threats.
The sandbox logs and marks malicious network traffic, processes, registry, and file modifications, providing immediate visibility into threat behavior.
Here’s a typical scenario of how you can use the connector in your SOC:
- Analysis: Analysts can send files or URLs for automated sandbox analysis directly from OpenCTI.
- Decision Making: Results from the sandbox analysis are used to assess threats and make informed decisions.
- Response and Escalation: Based on the results, analysts can isolate threats, block malicious activities, or escalate incidents as needed.
- Reduced manual effort with analysis automation.
- Higher detection rate with deep insights into threat behavior.
- Shorter MTTR with fast identification of malware and detailed reports for informed mitigation.
Enrich Incidents with Live Attack Data from 15K Organizations via Threat Intelligence Lookup
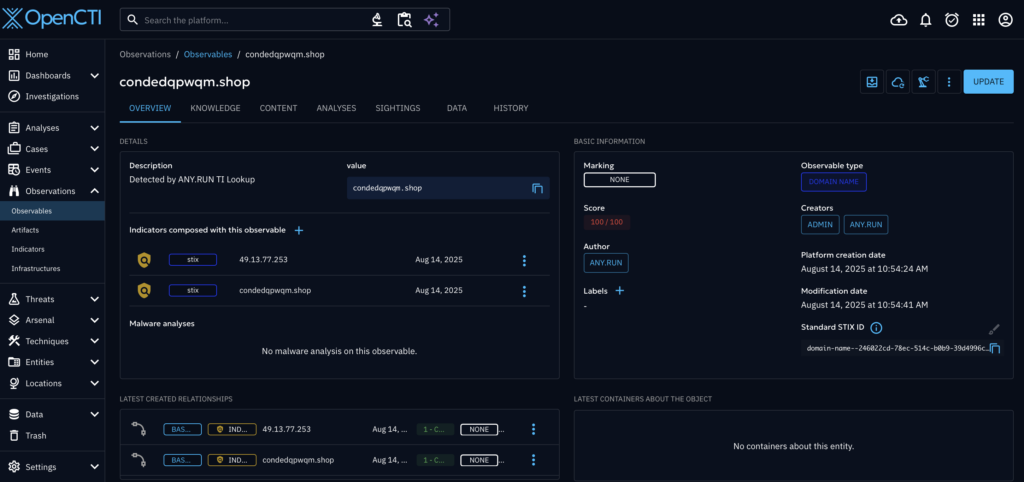
ANY.RUN’s Threat Intelligence Lookup provides a searchable database of fresh Indicators of Compromise (IOCs), Behavior (IOBs), and Action (IOAs). This data is extracted from live sandbox analyses of active malware and phishing attacks across 15,000 organizations, ensuring the indicators are fresh and available quickly after an attack.
With the OpenCTI connector, SOC teams can:
- Browse indicators in TI Lookup without leaving OpenCTI
- Receive data related to URL, IP, domain, and hash observables to gain actionable insights
- Use collected intel for incident response, to create new rules, train models, update playbooks, etc.
Use documentation to set up the connector →
Here’s a typical scenario of how you can use the connector in your SOC:
- Incident Enrichment: Analysts use TI Lookup to enrich incidents with detailed threat intelligence directly from OpenCTI.
- Threat Assessment: Analysts rapidly assess threats using up-to-date data and behavioral context.
- Response and Process Improvement: Enriched data aids in creating effective rules, updating playbooks, and improving detection models.
- Automatic incident enrichment by pulling detailed threat intelligence for various indicator types.
- Adding behavioral threat context to indicators, providing a deeper understanding.
- Speeding up threat assessment using high-quality, up-to-date data.
Expand Threat Coverage and Proactive Defense with Threat Intelligence Feeds
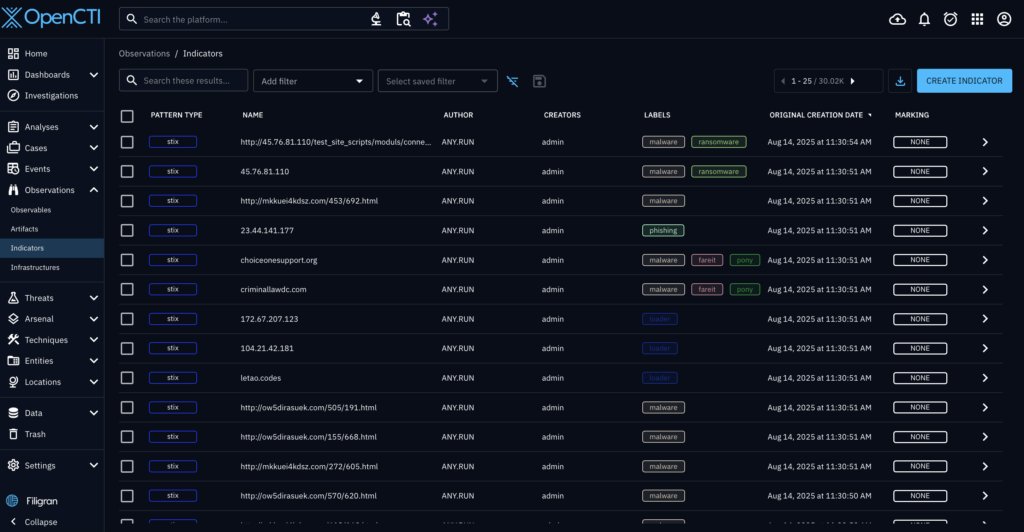
Threat Intelligence Feeds help MSSPs and SOCs fortify their security with filtered, high-fidelity indicators of compromise (IPs, domains, URLs) enriched with context from ANY.RUN’s Interactive Sandbox. Sourced from real-time sandbox investigations of active attacks across 15,000 organizations, ANY.RUN’s feeds are updated in real time, allowing you to track threats as they emerge, develop, and spread to take critical security actions early.
With the OpenCTI connector, SOC teams can:
- Retrieve real-time, up-to-date indicators and insights derived from attack investigations.
- Use ANY.RUN’s data in real-time or on a schedule as a source of malicious indicators for analyzing or investigating alerts and incidents.
- Send data to other security systems like SIEM or EDR, further improving detection quality.
Use documentation to set up the connector →
Here’s a typical scenario of how you can use the connector in your SOC:
- Expanded Threat Monitoring: Clients connect TI Feeds to OpenCTI to use real-time threat data for analyzing alerts and incidents.
- Detection and Response: Enhanced detection quality allows for better threat identification and response.
- Proactive Defense: Data from TI Feeds supports the creation of new rules, training models, and updating playbooks and dashboards.
- Proactive threat management by providing current and fresh data from active attacks.
- Improved quality of detection in various security systems.
- Enhanced ability to identify threats at earlier stages.
How OpenCTI Connectors Can Help Your Business
The interoperability of ANY.RUN with OpenCTI provides significant user and business value, leading to measurable performance gains across the SOC.
- Reduced costs and time savings by eliminating the need for custom development and allowing analysts to focus on critical threats.
- Increased SOC efficiency through streamlined triage, investigation, and escalation for Tier 1 and Tier 2 analysts.
- Automation of routine tasks, such as manually copying artifacts or launching analyses, which reduces analyst burnout.
- Reduced Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR), enhancing overall SOC metrics.
- Enhanced decision-making and process improvement by providing detailed reports and enriched data for creating effective rules, updating response playbooks, and training detection models.
- Proactive threat management and early threat detection by uncovering stealthy or multi-stage attacks that traditional tools might miss.
- Stronger ROI from existing tools by extending the capabilities of OpenCTI with behavioral analysis and contextual enrichment without additional infrastructure.
About ANY.RUN
Trusted by over 500,000 cybersecurity professionals and 15,000+ organizations in finance, healthcare, manufacturing, and other critical industries, ANY.RUN helps security teams investigate threats faster and with greater accuracy.
Our Interactive Sandbox accelerates incident response by allowing you to analyze suspicious files in real time, watch behavior as it unfolds, and make confident, well-informed decisions.
Our Threat Intelligence Lookup and Threat Intelligence Feeds strengthen detection by providing the context your team needs to anticipate and stop today’s most advanced attacks.
Ready to see the difference? Start your 14-day trial of ANY.RUN today →







0 comments