Before analyzing malware or dealing with the consequences of an attack the analyst needs to detect the threat. Unfortunately, with modern malware using so many anti-detection techniques, relying on automatic tools is not enough anymore.
In this post, we will talk about how ANY.RUN can help you detect malware where standard automatic systems fail.
Malware is Detected with Signatures
We use signatures to detect malicious programs. When threat actors took to the internet way in the past, they gained a way to distribute malware in horrifying quantities that security professionals couldn’t imagine at the time. In response, pioneers of the cybersecurity industry developed early AV software that incorporated what is now known as signature-based detection.
With signature-based detection, the AV software constantly analyses files and assigns a unique signature or hash to each. A hash is then added to the global online database. Antiviruses tap into that database and compare files against known hashes associated with malicious activity. If there is a match, the antivirus isolates the file.
Signature-based detection has been a staple of malware detection, but it’s slowly becoming less effective.
But Sometimes Signature-Based Detection is not Enough
Today, most malware samples are polymorphic. This means that they are equipped with a mutation engine that can change certain parameters like file names and hash sums, completely throwing off antiviruses. In other words, every instance of the same malware strain generates unique signatures, making it impossible to find a match in the signature-database.
Emotet Trojan and Qbot are examples of widely known malware families that use polymorphism.
One way to overcome the challenge is to use sandboxes. Sandboxes allow analysts to launch malware in a virtual environment and watch the execution process. This enables us to see exactly what the suspicious file will do on an infected machine and collect the data we need for identification.
The problem is that a lot of modern malware families use another evasion technique. They know when they are launched on a virtual machine and behave differently than they would in a real environment, thus avoiding detection.
This is where ANY.RUN comes in.
ANY.RUN’s Interactivity Throws-Off Malware Evasion Techniques
ANY.RUN can trick malware into executing as if it was launching on a real machine because our service is interactive. As a user, you can influence the simulation at any time and interact with the virtual environment: drag a mouse, tap keys, and so on. You can also control an extensive list of simulation parameters like setting up a virtual OS version.
With all of the above, the simulation can be corrected when a researcher notices that something strange is going.
Let’s Look at a Few Examples
ANY.RUN is a solid tool for malware identification. Let’s take a quick look at how you can use it to identify malware.
Imagine that we are analyzing a suspicious file in ANY.RUN. Every malware is different and creates different signatures. A good place to start is by looking at the network connections.
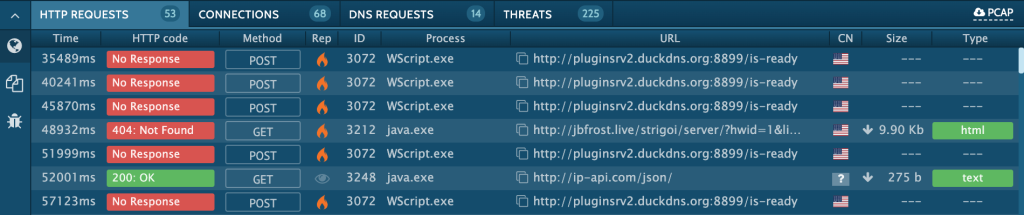
The network connections tab is at the bottom of the screen by default. Some malware strains connect with the C&C using the POST method. If you are lucky, you can find the malware strain in the user agent name.
Just click POST to open a pop-up window with additional details of the request.
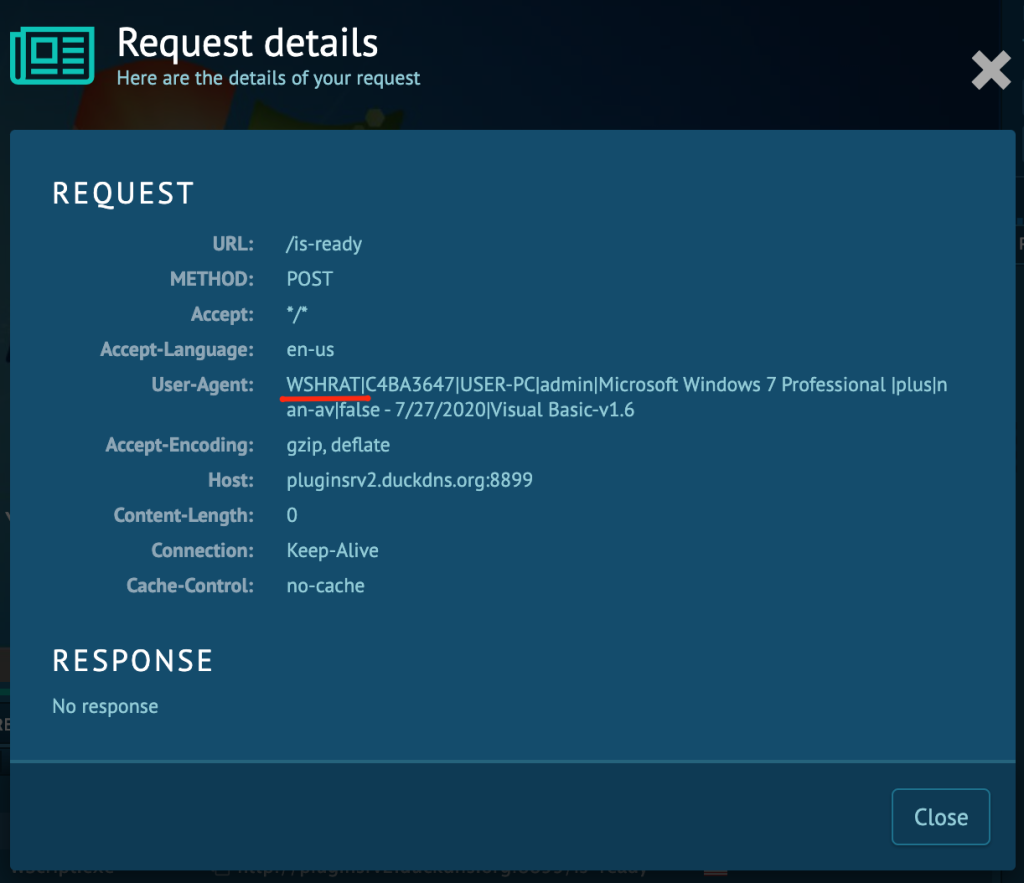
Sure enough, we got lucky and we can clearly see that we’re dealing with WSHRAT. As simple as that, we’ve identified the malware.
But network requests won’t work every time. Let’s take a look at one more example.
This time we don’t have any information in the HTTP requests, so we will have to look elsewhere.
Let’s take a look at the “Files tab” and search for file names associated with malicious behavior. The console will show us files created or modified by the malware.
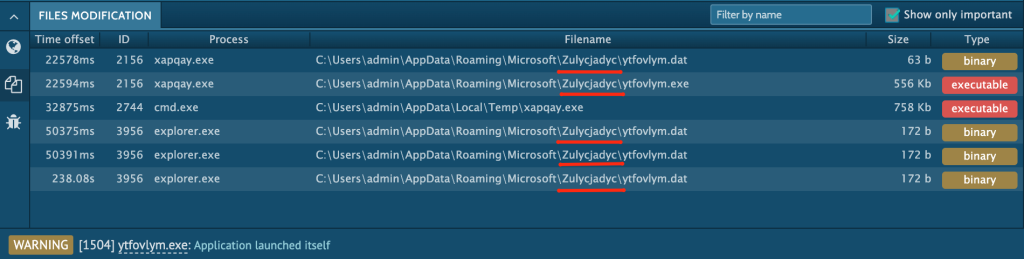
We can see a directory named “Zulycjadyc”. Usually, it is created by Qbot. We can say that we are dealing with this banking Trojan simply by finding the file or directory that it is known to generate.
In both cases, it would take us just a couple of minutes to analyze the file and identify the malware strain. Pretty impressive.
Conclusion
As malware is getting more advanced and automatic signature-based detection methods start to fail, we need new tools to identify malicious programs with a high degree of success. ANY.RUN can help researchers get results quickly when analyzing suspicious files and it will work where fully automatic sandboxes fail.
Next time that you come across a file that raises concerns, make sure to take a few minutes and run it through ANY.RUN!
3 comments







Hi there, simply changed into alert to your weblog via Google, and located that it is truly informative. I am going to watch out for brussels. I’ll be grateful in the event you proceed this in future. Many other people will be benefited out of your writing. Cheers!
Thank you. Im impressed. béèn searching fór hélp with thiß for a yéàr or moré. you gúys aré thé bést. mc
Thank you so much. Yes I’m ready to make a chañge in my life. Im excitéd and thànkful. mc