This is the June 2023 edition of ANY.RUN’s monthly malware analysis report, where we share key cybersecurity incidents from the last 30 days.
In June, cybercriminals use fake OnlyFans content to deploy DcRAT. The RecordBreaker malware spreads disguised as a .NET installer. North Korea’s APT37 group launches “FadeStealer” for cyber espionage. Crysis threat actors use Remote Desktop Protocol to deploy Venus ransomware, and more.
1. Fake OnlyFans Content Used to Deploy DcRAT Malware
A new malware campaign exploits the popularity of the content subscription service, OnlyFans, by using phony content and adult lures to install a remote access trojan (RAT) named DcRAT.
This RAT gives threat actors the ability to steal data and credentials or distribute ransomware on infected devices. The cybercriminals trick victims into executing a VBScript loader contained in a ZIP file, misleading them to believe they are accessing premium OnlyFans collections.
The infection chain for this campaign remains uncertain, but potential sources could include malicious forum posts, instant messages, malvertising, or Black SEO sites. The VBScript loader used is a minimally modified and obfuscated version of a script seen in a previous 2021 campaign. Upon launch, the loader verifies the OS architecture, extracts an embedded DLL file, and registers the DLL, gaining access to DynamicWrapperX — a tool for calling functions from Windows API or other DLL files.
Finally, the payload “BinaryData” is loaded into memory and injected into the “RegAsm.exe” process, a legitimate part of the .NET Framework less likely to be flagged by AV tools. This injected payload, DcRAT, is a modified version of AsyncRAT and has capabilities including keylogging, webcam monitoring, file manipulation, and remote access. Notably, it also has a ransomware plugin that targets all non-system files and appends the “.DcRat” filename extension to encrypted files.
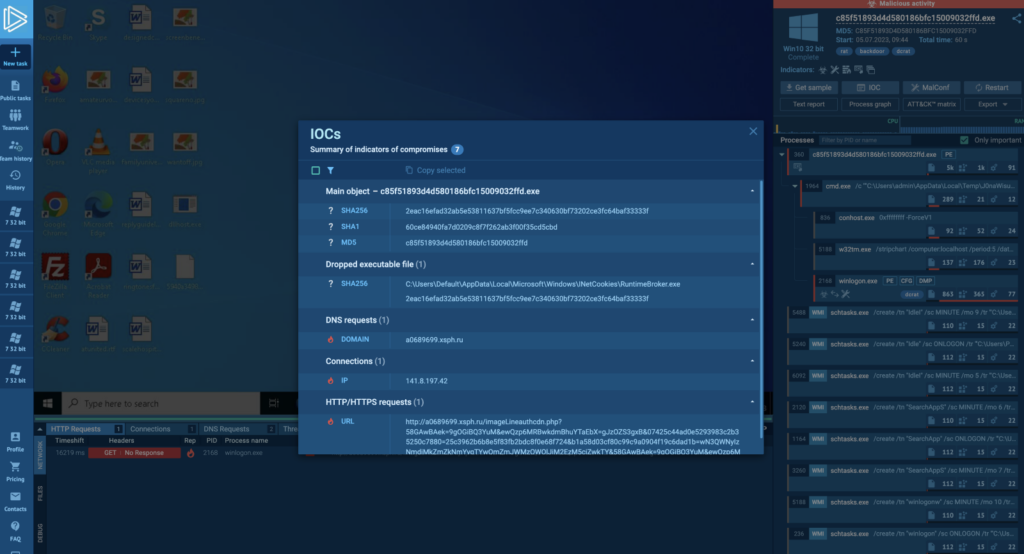
You can analyze DcRAT in ANY.RUN and easily collect IOCs from this malware.
2. RecordBreaker Infostealer Disguised as Legitimate Software
Innovative evasion techniques are being used by a new variant of the RecordBreaker (Raccoon Stealer V2) malware, which is now being disguised as a .NET installer. The malware employs a dual approach where, if executed in a virtual environment, it downloads a legitimate .NET update installer, deceiving sandbox-type analysis environments into classifying the file as benign.
However, in a typical user environment, a delayed execution command is triggered which downloads and executes an encrypted malware file from the C2 server. Once activated, RecordBreaker proceeds to steal sensitive user information and send it back to the server. Experts warn users to exercise caution when downloading files from unknown sources and to avoid using illegal tools like cracks or keygens.

If you want to learn more about Raccoon’s execution process, you can analyze it in ANY.RUN. View registry events, network activity, and extract a memory dump.
3. APT37 Group Deploys New FadeStealer Malware for Cyber Espionage
The North Korean hacking group APT37, also known as StarCruft, Reaper, or RedEyes, has begun utilizing a new “FadeStealer” malware, equipped with wiretapping features.
This malware allows the threat actors to steal sensitive data and record audio from victims’ microphones. In the past, the group targeted North Korean defectors, educational institutions, and EU-based organizations, deploying custom malware like “Dolphin” and “M2RAT” to extract information from Windows devices and linked mobile phones.
FadeStealer is typically delivered through phishing emails containing password-protected Word documents and a “password.chm” Windows CHM file. Upon opening the CHM file, a remote PowerShell script is downloaded and executed, establishing a backdoor that communicates with the attackers’ command and control servers. The malware “AblyGo backdoor” is also used in later stages of the attack for privilege escalation, data theft, and further malware delivery.
4. Crysis Threat Actor Deploys Venus Ransomware Via Remote Desktop Protocol (RDP)
AhnLab Security Emergency Response Center (ASEC) has detected that the threat actor behind Crysis ransomware is now deploying Venus ransomware via the Remote Desktop Protocol (RDP).
Both Crysis and Venus are significant types of ransomware known for targeting externally accessible remote desktop services. The actual logs from AhnLab Smart Defense (ASD) also demonstrate attacks being initiated through RDP, with additional tools such as Port Scanner and Mimikatz installed if the infected systems belong to a company’s internal network.
The threat actor utilizes RDP as an attack vector, scanning for systems with active RDP allowing external access. Systems discovered during this scanning process are susceptible to brute force or dictionary attacks, especially if the users have inadequate account credentials. Once the actor obtains these credentials, they gain control of the system and perform various malicious actions. The Venus ransomware installation was likely facilitated through RDP, evidenced by multiple malware types generated by the Windows Explorer process. Besides, the actor used the same Crysis ransomware to repeatedly launch attacks against other systems.
5. Microsoft Teams Bug Enables Malware Delivery from External Accounts
UK-based security services company, Jumpsec, has uncovered a flaw in Microsoft Teams that allows malware delivery from external accounts, bypassing the application’s established restrictions.
The communication and collaboration platform, with 280 million active users monthly, is susceptible to this vulnerability when running its default configuration, which permits communication with external Microsoft Teams accounts, also known as “external tenants.”
The researchers found they could circumvent client-side protections by modifying the internal and external recipient ID in a message’s POST request, thereby tricking the system into treating an external user as an internal one. This method enables a malicious payload to be delivered directly to a target inbox. Although Microsoft confirmed the existence of the flaw, they stated it “does not meet the bar for immediate servicing,” indicating a lack of urgency to rectify the issue. Consequently, Jumpsec advises organisations to either disable the external tenant feature or create specific domain allow-lists to reduce the risk of exploitation.
6. Job Application Letter Used as Malware Disguise
AhnLab Security Emergency Response Center (ASEC) has identified the ongoing distribution of malware masquerading as a job application letter.
The malware, capable of detecting various antivirus processes, is spread via malicious URLs designed to imitate a Korean job-seeking website. The downloaded file appears as a screen saver file extension (.scr) with an HWP document icon and contains a compressed data file.
Upon execution, the malware creates additional files by decompressing data in a directory and executes through InternetShortcut files. Normal-looking documents, such as a job application letter, are used to disguise the harmful actions of the malware. It initiates registry changes to continuously run the malware and performs malicious behaviors such as information theft and keylogging. The malware can execute a variety of actions based on the threat actor’s commands, such as configuring internet options, capturing screenshots, managing services, and checking internet cookie data. Users are advised to exercise caution, particularly with files disguised as Job Application Letter.scr.
7. MuddyWater Utilizes New PhonyC2 Framework in Attacks on Technion, PaperCut Servers
The Iranian-backed threat group MuddyWater, also known as Mango Sandstorm and Mercury, has been found using the PhonyC2 command-and-control framework in attacks against Israeli research institute Technion and PaperCut servers, as per The Hacker News.
PhonyC2, though bearing similarities to MuddyWater’s earlier MuddyC3 framework, has been undergoing regular updates to its tactics, techniques, and procedures, revealed a report from Deep Instinct.
Importantly, PhonyC2 is used to generate varying payloads that communicate back to the C2, awaiting operator instructions to conduct the final step of the ‘intrusion kill chain’. Initial access to compromised systems is vital for executing these PowerShell payloads, stressed Deep Instinct Threat Research Team Leader Mark Vaitzman. Some payloads are designed to maintain a persistent connection with the operator’s C2. Moreover, MuddyWater’s use of multiple C2 frameworks in its operations was also pointed out by Vaitzman.
Wrapping up June with ANY.RUN
Here at ANY.RUN, our team is always busy, rolling out new content and product updates.
We believe the only way to make the internet safer is by working together. That’s why we’ve started a new inbox to get your suspicious files and links submissions. Each one gets checked out, and if we find something new, we’ll add the detection rule to our sandbox. More about that here.
Talking about new stuff, this month ANY.RUN analysts have found what might be a new variant of the Gh0stBins RAT. We’ve put out a detailed technical analysis about its structure, communication protocol, and data exfiltration process.
Also, to help you sidestep sandbox evasion, we’ve added the option to set a residential proxy when you create new tasks. This gives a home user’s IP to your sandbox connections, so adversaries see your traffic as just another infected system. More on that in the update note.
Curious about more new things at ANY.RUN, like the latest extractors, detection rules and signatures added to the sandbox? Check it all out and more in our new format — monthly updated notes.
ANY.RUN is a cloud malware sandbox that handles the heavy lifting of malware analysis for SOC and DFIR teams. Every day, 300,000 professionals use our platform to investigate incidents and streamline threat analysis. Request a demo today and enjoy 14 days of free access to our enterprise plan.
1 comments







great article!