This article will explore how malware researchers, SOC teams, or DFIR team members can benefit from an interactive sandbox. We’ll also look at the advantages of this type of software.
What is an interactive malware sandbox?
It’s a virtual environment that allows you to perform actions in a virtual machine during execution, just as you would on a real system. This includes typing, clicking, pasting from the clipboard, and more.
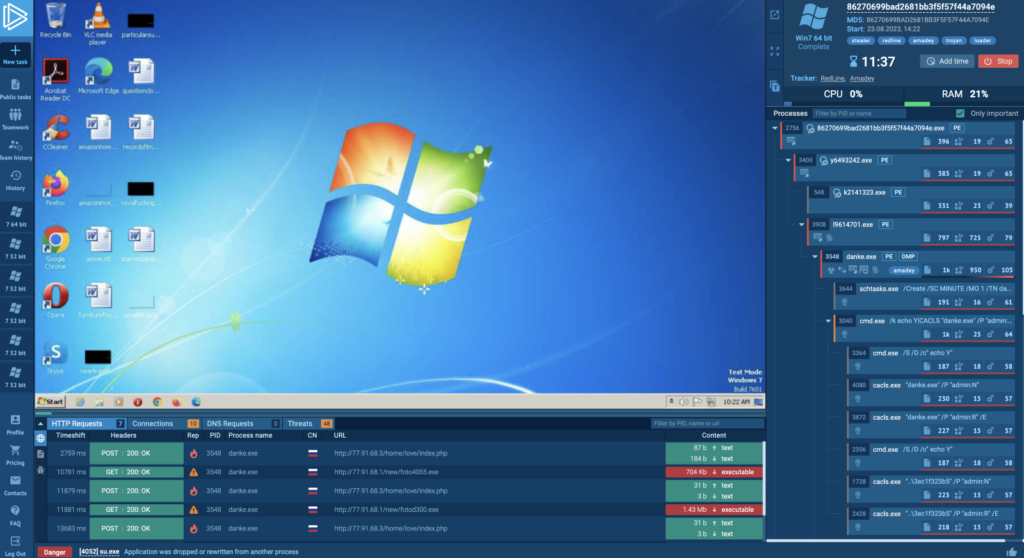
In ANY.RUN, users can interact with virtualized machines through their browser. Our cloud VMs are highly performant — there’s almost no latency during execution, and logging doesn’t introduce any slowdowns. This makes the user experience similar to working with a local setup.
Aren’t all sandboxes interactive? No. While some sandboxes offer an interactive mode, most leave the malware execution process behind the scenes, providing a report afterward. This method has its uses, but there are several disadvantages to this approach:
- You don’t have any visual representation of what happens in the virtual machine.
- You need to wait for the analysis to finish to get results.
- You don’t have any control over the emulation, so if the sample has anti-sandbox evasion techniques, it can avoid detection.
This is not to say that automatic sandboxes don’t have their use cases. For example, they allow you to process multiple files in batches.
Applying interactivity in the real world
At ANY.RUN, we’ve developed a sandbox focused on interactive analysis, aiming to simplify and expedite malware analysis.
Consider a case like DLL Hijacking
DLL Hijacking exploits the Windows dynamic-link library search order by placing a malicious DLL in a specific directory. The aim is to deceive an application into loading this rogue DLL instead of the legitimate one. This can happen when a user launches an application like a browser.
- Automatic sandboxes may fail to detect DLL Hijacking. While automatic sandboxes can identify malicious files, they may struggle with the behaviors resulting from DLL Hijacking. These environments generally scan individual files and may not capture the sequence of user or system events that trigger the rogue DLL.
- Interactive sandboxes provide more ways to trigger and detect DLL Hijacking. Analysts can manually initiate the application or system event, causing the rogue DLL to load. This allows for real-time capture of the DLL’s behavior and any C2 connections, providing a more thorough threat analysis.
Check the sample from our Public Submissions →
3 more use cases of interactivity in a malware sandbox
Here are 3 more ways how interactivity can aid in detecting malicious activity:
1. Opening password-protected archives
Embedding malware in a password-protected ZIP or RAR file is a common evasion tactic, often bypassing automatic sandboxes.
Automatic solutions can’t access encrypted content without the password, causing a stall or skip in analysis and letting malicious files go undetected. Interactive sandboxes don’t share this limitation; analysts can manually enter a password to access the encrypted content.
Check the sample from our Public Submissions →
2. Analyzing a phishing website
Phishing websites often require user interaction, such as submitting a form, clicking links, or downloading attachments, to reveal their true intent.
Automatic sandboxes are limited in simulating these user behaviors, which can lead to incomplete analysis or a miss. Interactive sandboxes, on the other hand, allow analysts to mimic real user actions.
Check the sample from our Public Submissions →
3. Copying and pasting to a virtual clipboard
There are instances where malware may actively interact with the clipboard, and understanding this behavior can be essential in analysis.
- Clipboard monitoring and data theft: most info-stealers monitor the clipboard for specific information, like Bitcoin addresses or credit card numbers. When such data is detected, the malware may send it to a remote server.
- Clipboard manipulation: certain types of malware might alter the content of the clipboard. For example, if a user copies a cryptocurrency address, the malware could replace it with an address controlled by the attacker.
- Triggered actions: some malware might require specific content to be present in the clipboard to execute a particular action or payload.
Direct access to the virtual machine clipboard may help us trigger the malicious behavior of a sample. And sometimes it is simply convenient: if you find an IOC in a virtual environment, you can easily extract it by copying it.
Check the sample from our Public Submissions →
Lets’s do a small research of Laplas Clipper together. Follow these steps:
- Send the crypto wallet address to the сlipboard, and paste it into the notepad.
- Wait for the tag laplasclipper to appear on the task, then we can be sure that the malware has started execution.
- Paste the wallet into the notepad again.
- And here we see the attackers have tampered with our crypto wallet address in the clipboard.
- Once we have the address of the attackers’ wallet, we can investigate further.
Key takeaways
Interactive sandboxes enable real-time analysis, visual representation of system activity, and more control over execution. In many cases, this helps detect malware that would have otherwise gone unnoticed.
Interactive sandboxes are useful:
- When real-time access to results is needed.
- For phishing investigation and if you encounter password-protected content.
- When you want to investigate a single object thoroughly
ANY.RUN is an interactive cloud malware sandbox. Every day, 300,000 professionals use it to investigate incidents and streamline threat analysis. You can try the benefits of interactive analysis for free — request a demo today and enjoy 14 days of free access to our Enterprise plan.









0 comments