Webinar
February 26
Better SOC with Interactive Sandbox
Practical Use Cases


Vidar is a dangerous malware that steals information and cryptocurrency from infected users. It derives its name from the ancient Scandinavian god of Vengeance. This stealer has been terrorizing the internet since 2018.
|
Trojan
Type
:
|
ex-USSR
Origin
:
|
|
1 December, 2018
First seen
:
|
8 February, 2026
Last seen
:
|
|
Type
:
|
ex-USSR
Origin
:
|
|
1 December, 2018
First seen
:
|
8 February, 2026
Last seen
:
|

 443
443
 0
0

 2320
2320
 0
0

 4485
4485
 0
0
Vidar is an information stealer trojan that was first identified in December 2018. It is either a fork of Arkei or the result of its evolution. Named after the god of vengeance from Scandinavian mythology, Vidar is used to steal information from infected systems, take screenshots, steal cryptocurrency, and more.
Vidar is presumed to have originated in a Russian-speaking country since the malware is configured to stop execution if it detects that it is being run on a machine that is located in one of the ex-USSR nations or on one that has a Russian keyboard layout.
Being another cyber threat that is available for purchase based on the MaaS (Malware-as-a-Service) business model, Vidar can be purchased on its “official” website for a hefty price tag of $700, at least for the PRO version. Though, a stripped-down version of the malware can be obtained for just $250.
According to the Vidar trojan analysis, malware is written in the C++ programming language. Purchasing account grants the attacker access to a control panel where the cybercriminal can set up the infostealer malware to target particular information on the victims’ PC. Like Arkei, cybercriminals need to take precautions to secure the main payload themselves, using crypto or a packer. The control panel displays the current builder version, user settings, malware status, and logs. It should be noted that Vidar data stealer uses domain names to search for C&C servers, where stolen data is being dropped, changing every four days. Though they are steadily changing, a constant response is required.
Vidar is capable of stealing text files in multiple formats, browser cookies and history, browser records, including data from TOR, as well as autofill value information, including banking and credit card details. Based on the Vidar analysis, the stealer malware can search for cryptocurrency wallet information, take screenshots and act as a message stealer, recording private messages from various software.
What’s more, Vidar is also known to be able to steal digital coins from offline wallets. In fact, holders of Litecoin, Bitcoin, Ethereum, Zcash, and DashCore are in potential danger, as these are the cryptocurrencies currently supported by this infostealer malware.
After collecting all targeted information, this stealer malware archives it and sends the stolen data to a control server, after which Vidar removes traces of its work and deletes itself from the system.
An analysis recorded in ANY.RUN malware hunting service allows us to take a closer look at the lifecycle of Vidar and perform Vidar analysis.
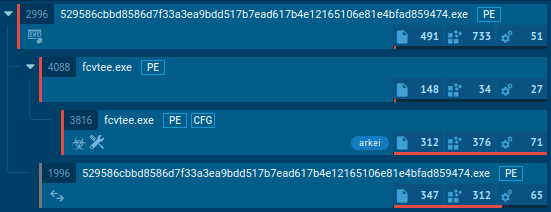
Figure 1: A visual process graph generated by ANY.RUN
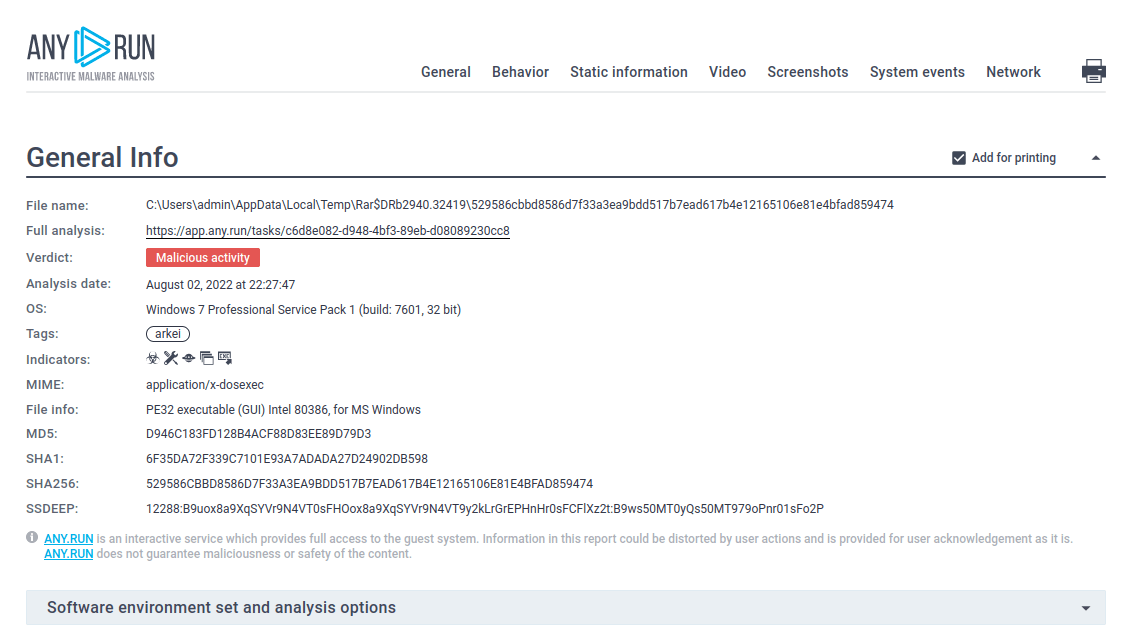
Figure 2: The customizable text report provided by ANY.RUN is a perfect tool to share the results of an analysis
According to the Vidar analysis, after the user downloads and runs a malicious file, it spawns a child process and collects information from the infected system. Often, after the information was collected, the malware kills and deletes itself from the system through a command-line command.
When spread via spam email campaigns like NanoCore or Agent Tesla, the Vidar stealer requires the user to download and run a malicious file to enter an active state and begin execution. Therefore, following some basic cybersecurity rules can ensure that users will stay safe from Vidar malware and the incident response team will work effectively.
As such, users should be careful when downloading attachments in emails from unknown senders. The best practice is to avoid downloading such files altogether, therefore not putting oneself in danger at all.
In addition, downloading only licensed software from trustworthy sources and avoiding gaming hacking clients greatly reduced the risk of being infected with malware such as Vidar trojan, which uses these attack vectors to infect victims.
According to the Vidar trojan analysis, Vidar is distributed through spam email campaigns as a malicious attachment, like other malware. In addition, cases of Vidar being distributed using shady software and gaming hack clients have also been recorded. Vidar infostealer targets users all over the world, except some ex-USSR countries, including Russia.
Some malware creates files in which it named itself. You can find such info about Vidar trojan using ANY.RUN's Static Discovering during your Vidar analysis. Open either the "Files" tab in the lower part of the task's window or click on the process and then on the "More Info" button in the appeared window. After that, all you need to do is click on the file.
 Figure 3: Vidar's log file
Figure 3: Vidar's log file
Vidar is a hazardous information stealer trojan, distributed as malware as a service. Thanks to its extensive stealer feature set, Vidar trojan can be used to retrieve a wide variety of information, including stealing select cryptocurrency coins from the users. Additionally, Vidar is capable of stealing data from TOR.
Thankfully, malware hunting services like ANY.RUN allows researchers to conduct extensive studies of malware samples in a secure environment, allowing them to spread information about the danger and develop effective countermeasures and incident response.
Create your free ANY.RUN account to analyze malware and phishing without limits!





