There’s a new phishing campaign delivering STRRAT and VCURMS Remote Access Trojans through a malicious Java-based downloader, which we can observe on ANY.RUN.
STRRAT is a Java-based Remote Access Trojan (RAT) that primarily functions as a keylogger, extracting credentials from browsers and applications.
VCURMS is another RAT, possibly connected to the Rude Stealer malware. It runs cmd.exe commands, collects system data and credentials from browsers, Discord, Steam, and other programs. It can also upload additional modules to expand its information-stealing functionality as needed.
The attack chain begins with a phishing email urging recipients to click a button to verify payment information. Clicking this button downloads a malicious JAR file disguised as a payment invoice. This file then downloads and runs two more JAR files to launch the VCURMS and STRRAT trojans.
Uniquely, the attackers store the malware files on AWS or Github and use commercial protection to hide their malicious nature. The initial JAR file delivered via email is obfuscated and downloads the malware using a PowerShell command.
Finding the attack in ANY.RUN’s Threat Intelligence Lookup
We can use ANY.RUN’s Threat Intelligence Lookup to first find samples of this campaign, confirm the reported behavior, and collect IOCs and malware configuration extracted from memory.
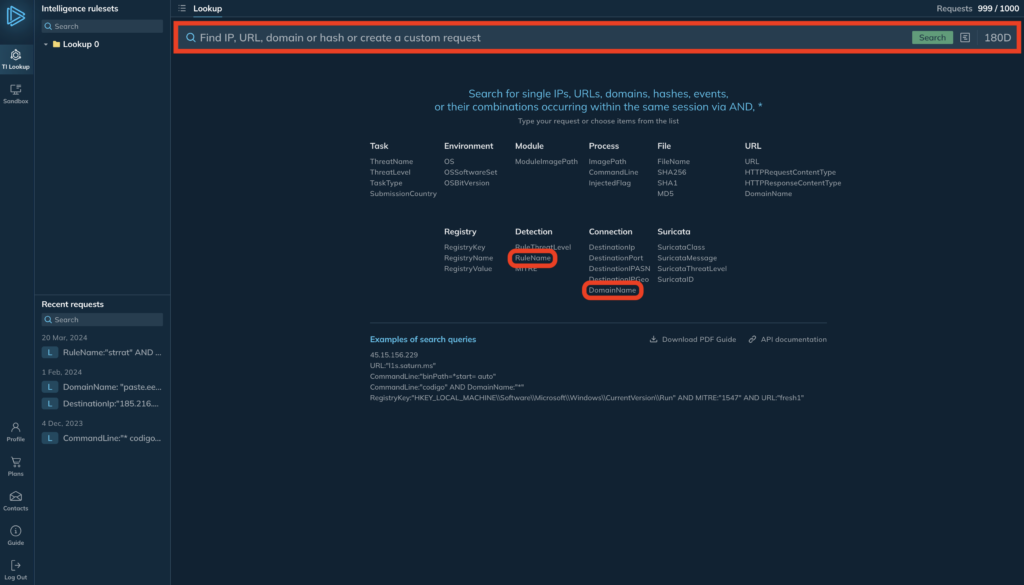
In the ANY.RUN TI Lookup, we can use the query constructor to build our query: ‘RuleName:”strrat” AND DomainName:”github.com”’.

Let’s execute the query and see what we can find. The lookup provides several interesting results:
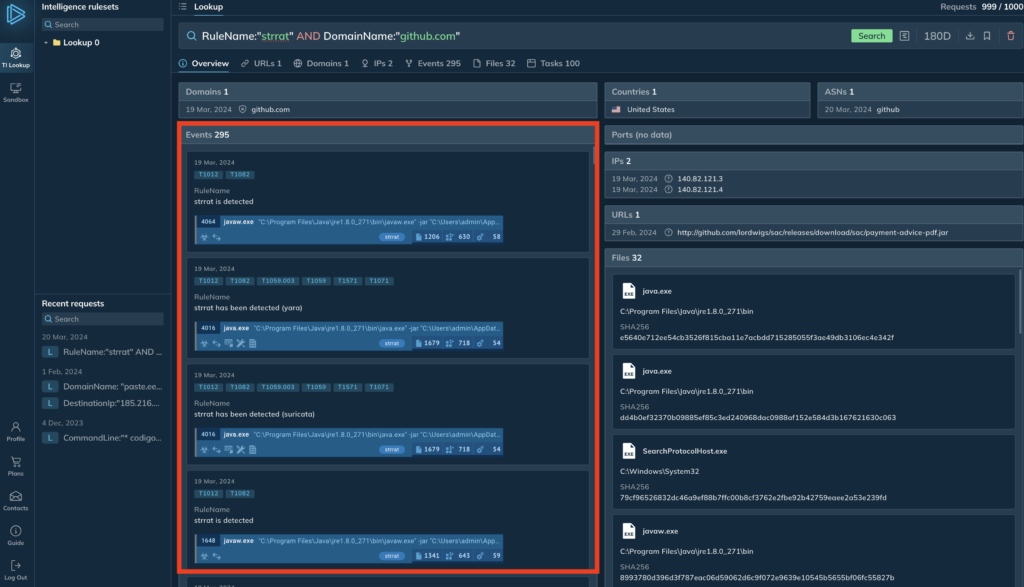
- In the left table (marked with a red border), we can see related events. These are interactive sandbox research sessions where the ANY.RUN sandbox detected STRRAT. We can use them to analyze a malware sample in a realistic environment.
- On the right is a list of malicious executable files, which you can download for reverse engineering or take their hashes directly to investigate your logs or enrich related objects in your security systems.
Analyzing the attack in ANY.RUN’s Sandbox
Let’s open a recording of an interactive research session to study the sample’s behavior and collect more IOCs from it.
You can browse to this research session to follow along.
You will see a recording of a virtual machine session. First, note the top-right corner, where the general information is displayed:
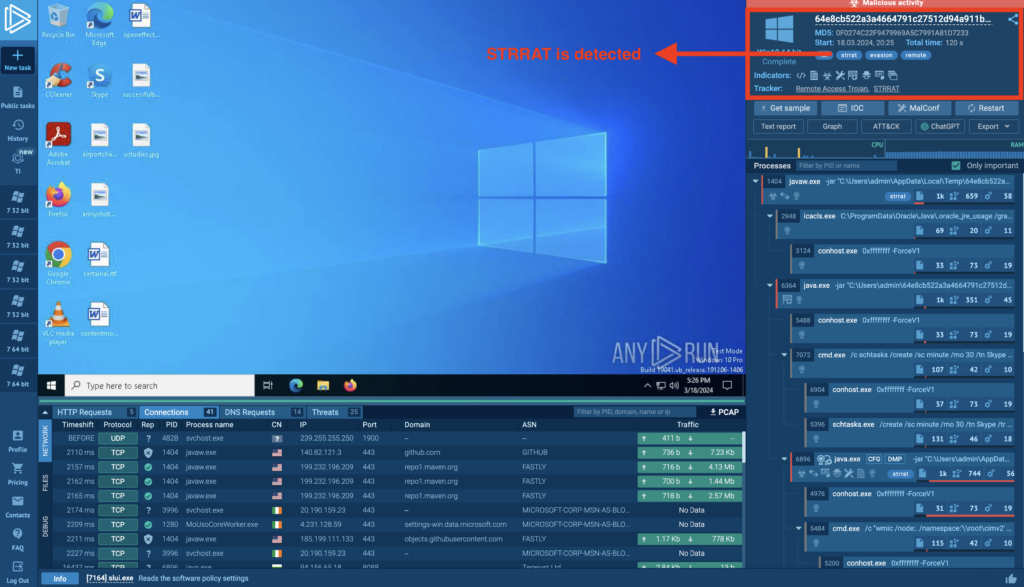
The main view in the ANY.RUN interactive sandbox shows tags in the upper-right corner. We can see that STRRAT was detected. At the bottom of the screen, there is a connections tab. We can use it to see which processes communicated with what resources. Is there anything interesting?
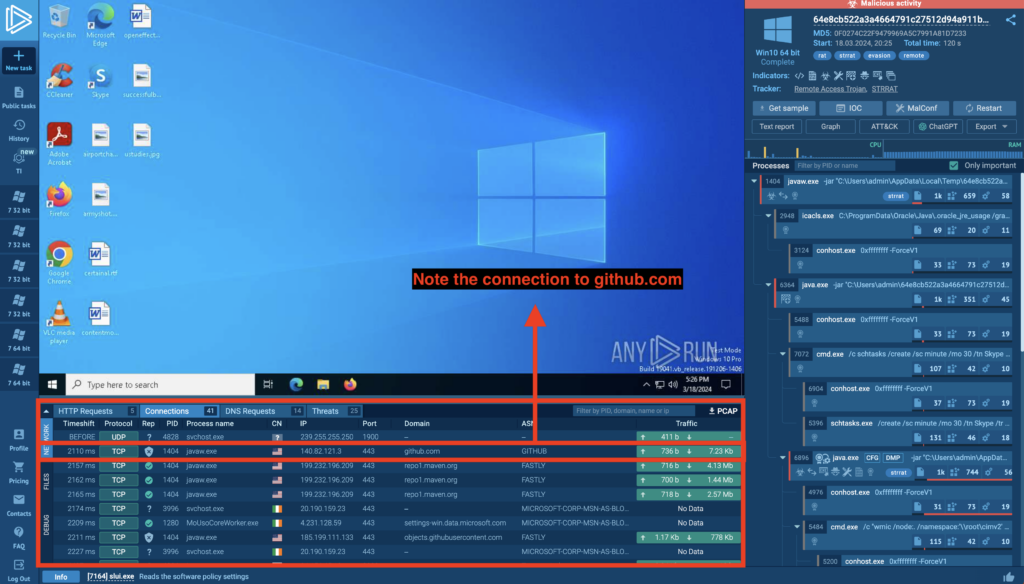
We can see that an executable javaw.exe established a connection to GitHub — this confirms that the sample we’re reviewing is part of the same campaign. We can then quickly and efficiently do two things:
- Collect the malware’s IOCs.
- View its configuration.
ANY.RUN has specialized reports for both of these actions. Let’s start by collecting IOCs:
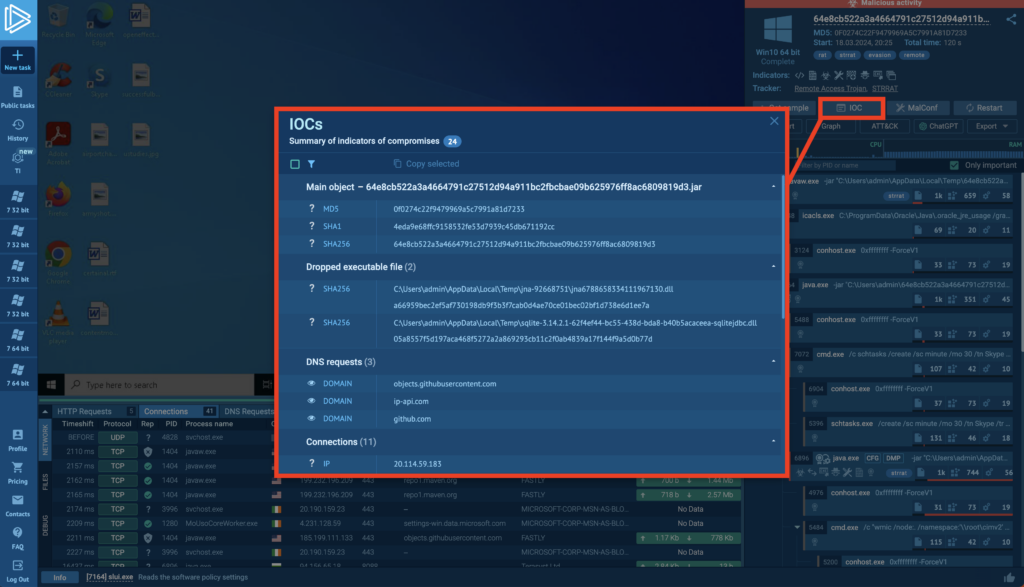
The IOC button in the upper right opens this report. You can use this information to configure security systems or investigate further.
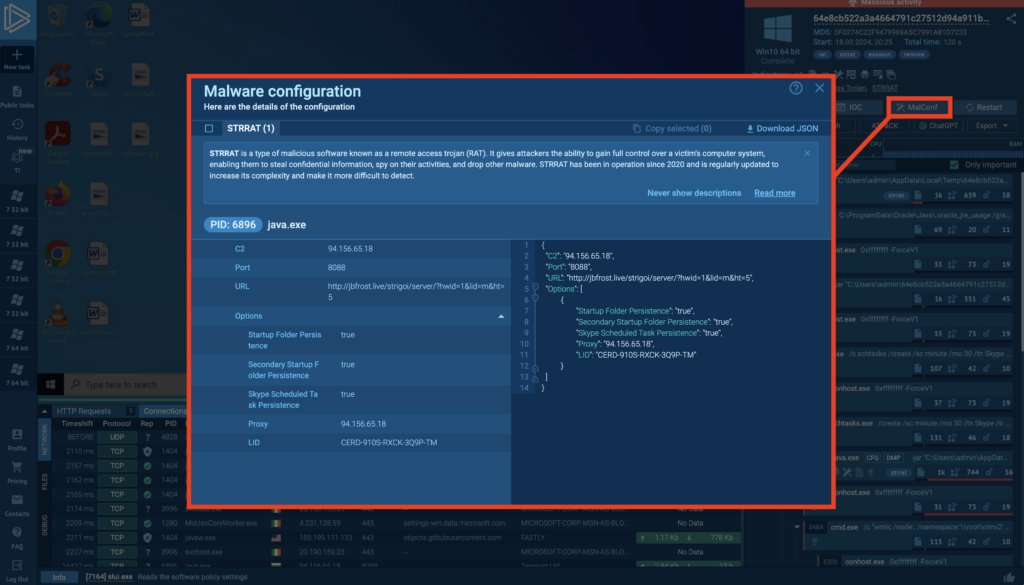
Saving the best for last, ANY.RUN can automatically extract malware configuration of many families from memory and from encrypted traffic. Often, you can access decrypted strings without manually reverse-engineering the sample.
The screenshot above shows the configuration of our sample: note how it established persistence, and the location of the C2 in the right part of the popup window.
About ANY.RUN
ANY.RUN’s interactive sandbox is trusted by over 400,000 cybersecurity professionals worldwide. We streamline analysis of Windows and Linux malware. Our threat intelligence products, including Lookup and Feeds, deliver indicators of compromise and deep contextual insights, helping to detect and respond to emerging and persisting threats.
ANY.RUN’s Benefits for Enhanced Threat Analysis
ANY.RUN provides numerous benefits to businesses seeking to enhance their threat analysis capabilities. These include:
- Quick malware detection: ANY.RUN can detect malware and identify many malware families using YARA and Suricata rules within approximately 40 seconds of uploading a file.
- Interactive analysis: ANY.RUN’s interactive capability allows you to interact with the virtual machine directly through your browser, making it a convenient tool for analyzing sophisticated malware without leaving your browser.
- Scalability: ANY.RUN’s cloud infrastructure enables businesses to scale their threat analysis capabilities as needed, providing flexibility and adaptability to changing business needs.
- Collaboration: ANY.RUN allows security teams to collaborate and share analysis results, improving communication and streamlining the threat analysis process.










0 comments