You’ve likely noticed that ANY.RUN interactive malware sandbox very effectively flags emails with phishing tags. We utilize proprietary detection rules to identify suspicious emails, providing analysts with a straightforward method to determine when a message warrants further investigation through Static Discovering.
However, in rare instances, there are phishing emails that our rules don’t cover. For such cases — and when you wish to analyze an email in great depth to better understand if it poses a risk to your organization — we’ve introduced a new module to Static Discovering: the RSPAMD module.
(To simplify email analysis, we’ve also incorporated an HTML content preview of the email in question.)
RSPAMD module is now available in ANY.RUN
When you open an email file in Static Discovering, you will automatically see the RSPAMD tab. Clicking on it reveals a detailed breakdown of the email’s information, including its spam score, headers, and RSPAMD symbols.
The information displayed is interactive; you can expand the tree and delve into multiple levels to conduct thorough investigations of the email content — a feature previously missing to this extent in ANY.RUN.
What is RSPAMD?
RSPAMD is a powerful, open-source email filtering system designed to identify spam, phishing attempts, and other malicious email content. It employs a mix of techniques such as regular expressions, statistical analysis, and machine learning algorithms. The system evaluates the email’s content, its headers, and the sender’s reputation to assign a spam score to each message — the higher the number, the more confident the system is about the malicious nature of an email.
Features of RSPAMD
RSPAMD offers access to a wide range of useful information. It’s helpful for in-depth analysis of suspicious emails. This information includes:
- Symbols: Each test that RSPAMD performs on an email generates a symbol. These symbols represent specific checks, such as found spam keywords, known malicious URLs, suspicious email patterns, and many others. By reviewing which symbols were triggered, you can understand why RSPAMD rated an email in a particular way.
- Header analysis: Detailed examination of the email’s header information, revealing the path the email took across the internet, the authenticity of the sender (through SPF, DKIM, and DMARC checks), and any anomalies that might indicate spoofing or other malicious tactics.
- Reputation checks: Information on the sender’s IP and domain reputation, utilizing DNSBLs (DNS-based Blackhole Lists) and URIBLs (Uniform Resource Identifier Black Lists) to identify known sources of spam and malware.
- Bayesian filtering: Probabilistic analysis based on the email’s content, comparing it to known good (ham) and bad (spam) emails to determine its classification.
Using the RSPAMD module in ANY.RUN
In addition to the existing static analysis modules, such as EMAIL, the new RSPAMD module further enhances our ability to analyze emails, offering additional tools for determining whether an email poses a threat to your organization.
At the time of implementation, the module provides advisory information. RSPAMD analyzes the email and offers a detailed description of any ambiguities.
Without even opening anything on a virtual machine, analysts can understand that the email is dangerous and should be taken seriously.
But by looking inside the email, you can clarify the exact issues, as the description covers both the email as a whole and specific contentious points, highlighting the problems. By clarifying these ambiguities, you can decide whether to trust the email.
Example: Email 1
Let’s look at a case study.
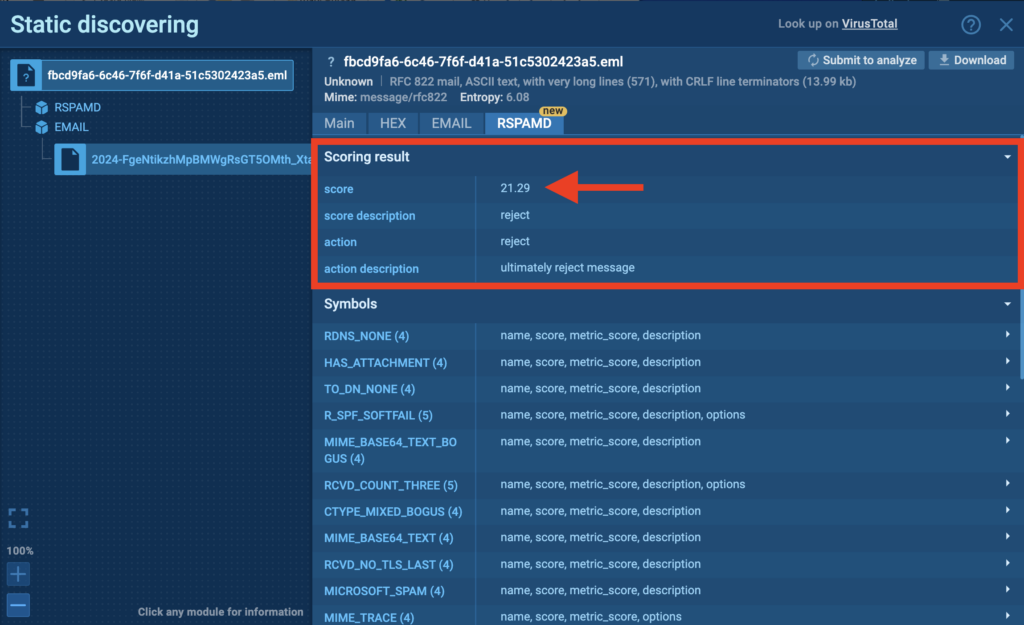
As shown in this task (above) you immediately get access to the email’s score, calculated by a formula that gives you a general idea of the email’s nature. With a score above 20, you can preliminarily deem an email undesirable, but let’s dig deeper.
Thanks to RSPAMD, we can find out if the email contains text parts encoded in base64, a short HTML part with a link to an image, and if the “From” header display name contains excess whitespace, unknown client hostname (PTR or FCrDNS verification failed) and a lot more information which may be hidden inside email.
Example: Email 2
Let’s consider another case.
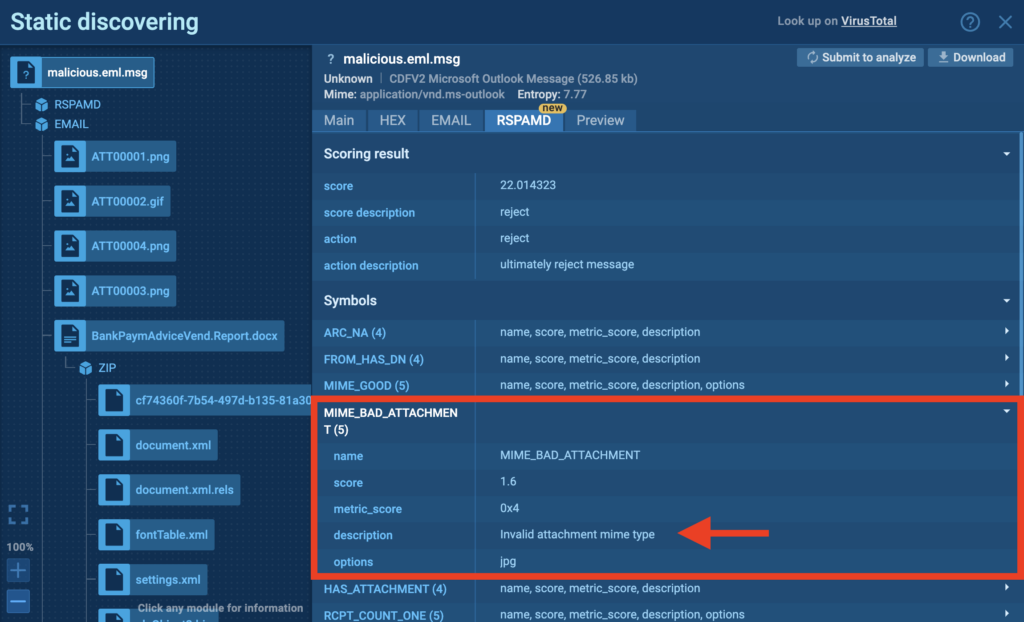
We notice that this email (shown above) has a score above 20 and an invalid attachment MIME type. The content of the email influences its characteristics. Exploring further we see that structure of the headers in this email is likely broken. It already looks suspicious. But by taking a deeper look inside we can find out the nature of the threat.
By using interactivity to open the attachment, we can trace the entire infection chain, namely the exploitation of the CVE-2017-11882 vulnerability followed by the downloading of malicious software and system infection by malware.
About ANY.RUN
ANY.RUN is a developer of cloud malware sandbox that handles the heavy lifting of malware analysis for SOC and DFIR teams, as well as Threat Intelligence Feeds and Threat Intelligence Lookup. Every day, 300,000 professionals use our platform to investigate incidents and streamline threat analysis.
Request a demo today and enjoy 14 days of free access to our Enterprise plan.






0 comments