From residential proxy to FakeNet and MITM proxy, ANY.RUN has consistently provided advanced network analysis tools since its launch. Our service empowers users to meticulously dissect malicious traffic and extract crucial information in seconds. Now, we’re elevating our capabilities by expanding the descriptions of threats detected by the sandbox and granting full access to triggered Suricata rules.
Redesigned Threats section
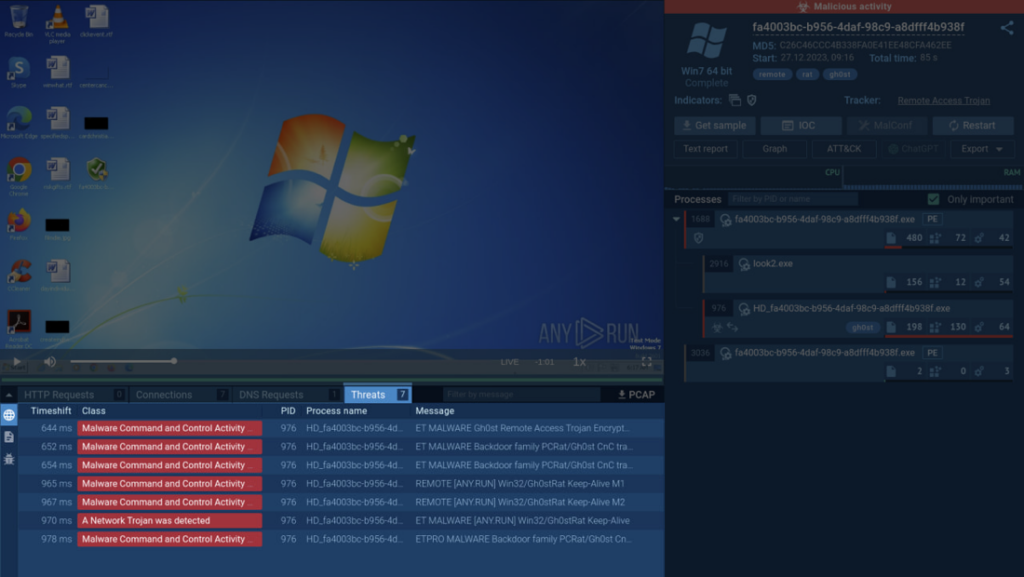
To enhance transparency into malware’s network activity, we’ve revamped the Threats section in ANY.RUN‘s interface.
Simply click the Threats tab right below the VM screen to access a complete list of malicious activities identified by the sandbox using Suricata signatures.
New Threat Details window
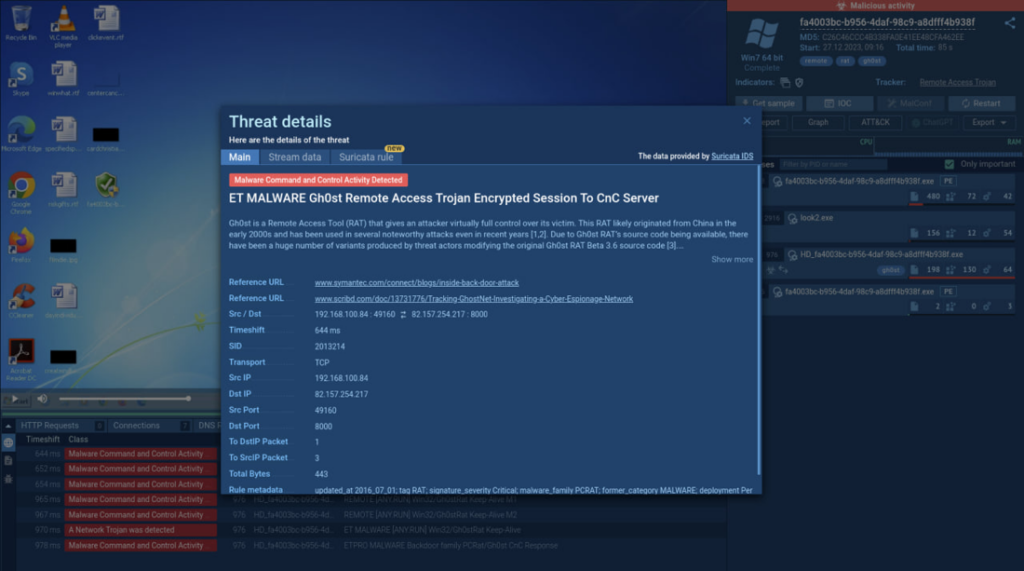
By selecting a specific threat, you’ll gain access to the Threat Details window, providing a comprehensive overview of the detected threat. This includes links to the original sources of threat intelligence, along with the source and destination IP addresses, ports, and the employed transport protocol.
The “Stream data” tab within the Threat Details window offers insights into malicious packet content. The downloadable data is presented in both hexadecimal format and human-readable text, enabling thorough analysis.
Viewable Suricata rules
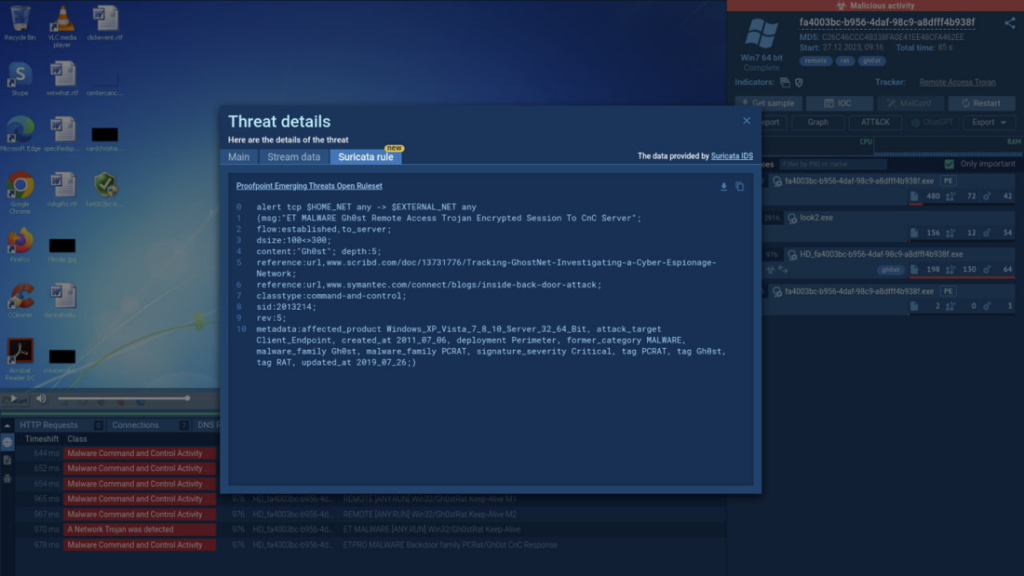
Exclusively for Hunter and Enterprise plan subscribers, the Suricata rule tab grants access to the signature content used for identifying the threat. This empowers users to witness firsthand how the ET Open rulesets align with various network activities.
Video demonstration
For a visual guide, we’ve created a helpful video based on this task that walks you through the process of accessing the redesigned Threat Details window and viewing Suricata rules.
To wrap up
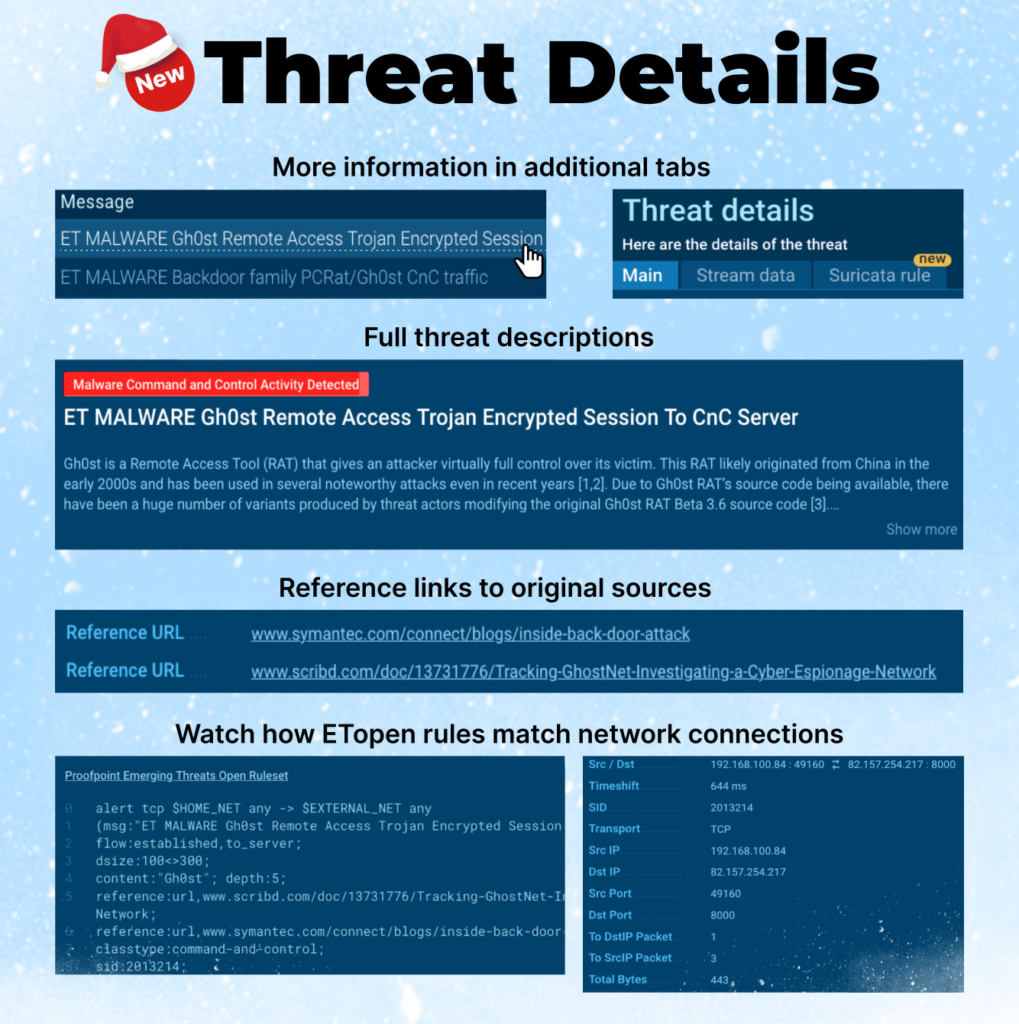
The new Threat Details window serves as a valuable addition to ANY.RUN’s interface, as it:
- Grants users access to essential information on the threats detected by the sandbox, including additional sources to expand their understanding.
- Lets users manually analyze the packet data and download it for further examination.
- Enables users to view the exact rule, which marked this network activity as malicious and see its insides.
About ANY.RUN
ANY.RUN is a cloud-based sandbox for advanced malware analysis that lets you investigate any type of file or link to identify if it poses any threat. The service streamlines the work of SOC and DFIR teams and is trusted by a diverse community of 300,000 professionals worldwide. Join their ranks with 14 days of free access to our top Enterprise plan.







0 comments