Welcome to the August 2023 installment of ANY.RUN‘s monthly report on malware analysis. In this edition, we highlight critical cybersecurity events from the past month.
In August, the US Justice Department led a global operation to neutralize Qakbot malware, seizing over $8.6 million in cryptocurrency and disrupting its botnet. LummaC Stealer employs Amadey for payload delivery, Raccoon Stealer returns with new features, a new macOS variant of XLoader disguised itself as an Office app to steal data, and more.
1. Qakbot Malware Neutralized in Global Operation
The US Justice Department, in collaboration with international partners, has disrupted the Qakbot botnet and malware.
This operation involved actions in multiple countries including the United States, France, Germany, and the Netherlands. The takedown led to the deletion of Qakbot malicious code from victim computers and the seizure of over $8.6 million in cryptocurrency.
Qakbot has been a primary infection vector for several notorious ransomware groups, including Conti and REvil. The operation also identified over 700,000 infected computers worldwide, effectively cutting them off from the Qakbot botnet.
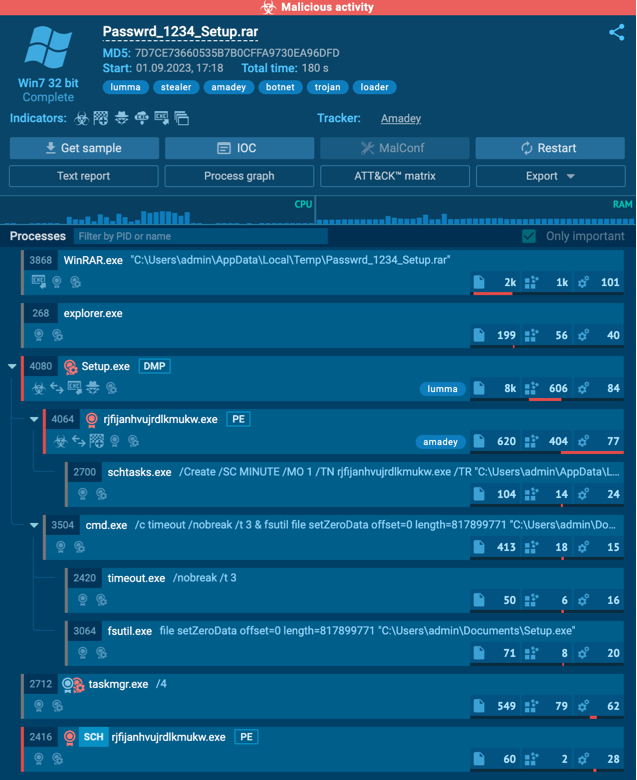
2. LummaC Stealer Uses Amadey Bot to Deploy SectopRAT in Multi-Stage Attacks
LummaC Stealer is at the forefront of a multi-stage malware campaign.
The stealer initiates by swiping sensitive data and then fetches the Amadey Bot for system assessment. Amadey Bot subsequently deploys SectopRAT, a Remote Access Trojan designed for data theft and remote control.
The campaign leverages Malware-as-a-Service (MaaS) platforms, making it easier for various threat actors to participate. The article provides a deep dive into the technical aspects of these malware strains and their infection chains.
Check the sample from our Public Submissions →
3. Raccoon Stealer Returns with New Features
Raccoon Stealer, a malware-as-a-service (MaaS) threat, is back with enhanced capabilities after a six-month hiatus.
The arrest of one of its main operators, Mark Sokolovsky, led to a temporary halt in its operations. The FBI has identified more than 50 million unique credentials from the data stolen by Raccoon. The malware is known for its low subscription cost and high return on investment, making it appealing to less sophisticated threat actors.
Raccoon has introduced new features like quick search for cookies and passes, automatic bot blocking, and a reporting system to block IP addresses used by crawlers and bots. These updates aim to make it easier for threat actors to find the information they need while making it harder for security tools to detect the malware.
4. DreamBus Malware Targets RocketMQ Servers via Critical Vulnerability
A new version of the DreamBus botnet malware is exploiting a critical remote code execution vulnerability in RocketMQ servers. The vulnerability, identified as CVE-2023-33246, affects RocketMQ version 5.1.0 and older.
The malware uses the ‘interactsh’ open-source reconnaissance tool to identify software versions on internet-exposed servers. It then downloads a malicious bash script named ‘reketed’ from a Tor proxy service, evading detection from AV engines on VirusTotal.
DreamBus focuses on Monero mining but its modular nature could allow for expanded capabilities in the future. RocketMQ servers are commonly used in communications, so the attackers could potentially tap into sensitive conversation data for greater monetization.
5. Fake Browser Updates Lead to NetSupport RAT Infections
Trellix researchers have identified a campaign using fake Chrome browser updates to deliver NetSupport Manager RAT.
The campaign leverages compromised websites to present fake Chrome updates, enticing victims to install the remote administration tool. The tactics are similar to those used in a previously reported SocGholish campaign but with some differences in the deployed tools.
The campaign uses a mix of batch files, VB scripts, and the Curl tool to download and install the RAT, making it more challenging for endpoint solutions to detect this attack.
Check the sample from our Public Submissions →
6. MacOS XLoader Variant Disguises Itself as Office App
SentinelOne researchers have spotted a new macOS variant of the XLoader malware.
Unlike its previous Java-dependent versions, this one is written in C and Objective C and was signed with an Apple developer signature.
The malware masquerades as an office productivity app called OfficeNote. It aims to steal browser and clipboard secrets, targeting users in work environments. Despite Apple revoking the signature, XProtect still doesn’t prevent its execution.
7. KeePass Vulnerability Exposes Master Passwords from Memory
A new vulnerability in the open-source password manager KeePass allows attackers to extract master passwords directly from the software’s memory.
The vulnerability, identified as CVE-2023-32784, affects versions prior to 2.54 of KeePass 2.x. It exposes the risk of malicious actors recovering the clear text master password from various memory sources, including process dumps and hibernation files. A proof-of-concept tool demonstrating the exploit has been posted on GitHub.
While the exploit requires local access to the user’s system, it raises concerns about the security of password managers. KeePass plans to issue a patch by early June to address this vulnerability.
8. LLM-Themed Facebook Ads Spread Profile Stealers
Threat actors are using Facebook ads themed around Large Language Models (LLMs) to distribute malicious browser add-ons. These add-ons aim to steal victims’ credentials.
The campaign uses paid Facebook promotions and URL shorteners like rebrand.ly to lure victims. Once clicked, the ads redirect to websites offering an “AI package,” which is actually a malicious file hosted on cloud storage services like Google Drive and Dropbox. The file, when executed, installs a malicious Chrome extension designed to steal Facebook cookies and access tokens.
Meta has removed the fraudulent pages and ads. However, the threat actors appear to be targeting business social networking managers or administrators, exploiting their interest in AI technologies for malicious gains.
9. BlackCat Ransomware Evolves with Impacket and RemCom Tools
A revamped version of BlackCat ransomware now incorporates Impacket and RemCom tools for enhanced lateral movement and remote code execution.
The malware uses Impacket for credential dumping and remote service execution, facilitating broader deployment in target environments. It also embeds the RemCom hacktool for remote code execution and contains hardcoded compromised target credentials for lateral movement.
This new variant follows an updated version called Sphynx, which emerged earlier this year with improved encryption speed and stealth. The group behind BlackCat continues to evolve, recently releasing a data leak API to increase the visibility of its attacks.
10. Gootloader Malware Targets Law Firms via SEO Watering Hole
Gootloader malware is exploiting SEO techniques to target law firms and individuals searching for legal information.
The malware manipulates search engine results to direct users to compromised WordPress sites. Once there, users are lured into downloading malicious files disguised as legal documents. Trustwave’s SpiderLabs reports that nearly 50% of these attacks focus on law firms, and the malware has a multilingual reach, targeting English, French, Spanish, Portuguese, German, and South Korean languages.
Gootloader is unique in its approach, using SEO to lure victims rather than relying on traditional phishing methods. This technique allows for a high volume of specific data sets, making law firms particularly vulnerable due to the sensitive information they handle.
Wrapping up August with ANY.RUN
At ANY.RUN, the team has heavily focused on network rules—adding 120 new Suricata rules in August—thereby significantly expanding ANY.RUN’s threat coverage.
Being able to automatically extract configuration files is one of the major advantages of our sandbox. In August, new config extractors for three malware families were introduced:
- Lu0Bot
- Strela
- RaccoonClipper
The LummaStealer extractor received a major update to improve detection of its latest versions. Updates were also made to the LaplasClipper, RaccoonStealer, and StealC extractors, among others.
ANY.RUN boasts industry-leading detection capabilities, but we’re not stopping there and continually working to improve them even further. That’s why, in August, the team overhauled the detection logic for malicious IPs, URLs, and domains, making it even more robust that before.
Interested in learning more about the latest ANY.RUN updates? Read our monthly release notes.
ANY.RUN is a cloud malware sandbox that handles the heavy lifting of malware analysis for SOC and DFIR teams. Every day, 300,000 professionals use our platform to investigate incidents and streamline threat analysis. Request a demo today and enjoy 14 days of free access to our enterprise plan.







0 comments