As annoying as they may be, Windows updates are necessary. They contain new features, bug fixes, and security updates. Thus, it makes sense for a bad actor to use these updates and sneak malware into your system.
In fact, Windows updates occur so frequently that we often mindlessly accept them without prejudice. It’s a testament to our trust in Microsoft (and impatience). Bad actors can use fake Windows updates to exploit this trust—after all, the best place to hide poison is in our medicine.
But how do bad actors circumvent Microsoft’s strict security controls and launch fake Windows update campaigns? What are the dangers and how do you protect yourself? The following article will answer these questions and provide tangible solutions.
Understanding and Identifying Malicious Fake Updates
The nefarious designs behind fake updates often mirror common cyber attack techniques. By masquerading as legitimate software updates, cybercriminals exploit the familiarity factor of Windows (and Microsoft as a whole).
Understanding the modus operandi of such attacks, including the common techniques and targets, can equip users with the knowledge to discern legitimate updates from malicious ones. It’s a cat-and-mouse game where being informed is the user’s best defense.
First, let’s explore how fake updates work and the types of threats they may be harboring.
How Fake Windows Updates Work
These days, people don’t need much to launch a cyberattack. You can use seemingly innocuous websites to help you create fake software updates as a “prank”.
And it’s a concerning notion, since most modern exploits rely on social engineering, and tend to be a part of a multi-stage attack. Once the ball gets rolling, it can be quite difficult to address these threats individually, let alone all at once. Therefore, it’s essential to pinpoint threats as early as possible.
Threat Identification and Symptoms
A legitimate Windows update notification will display from the taskbar notification area (default behavior):
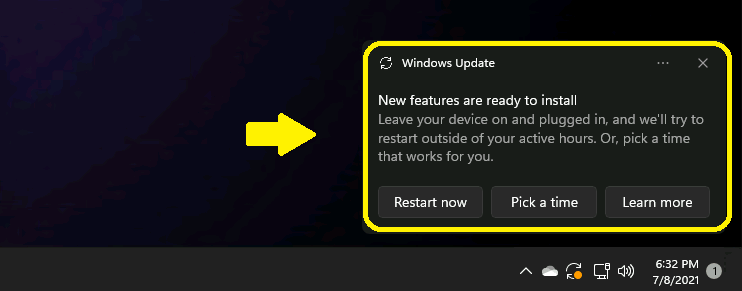
Look out for any update pop-up notifications that contain grammatical and spelling errors, do not follow your system’s theme (color scheme, size, and font), or originate from places they shouldn’t (like a web page).
If you suspect the notification is fraudulent, you can just click away from it. Windows Updates have their own special taskbar/tray icon that can be enabled or disabled. The icon has been the same since Windows 11 They can be ultimately used to verify Windows update notifications by right-clicking on it:
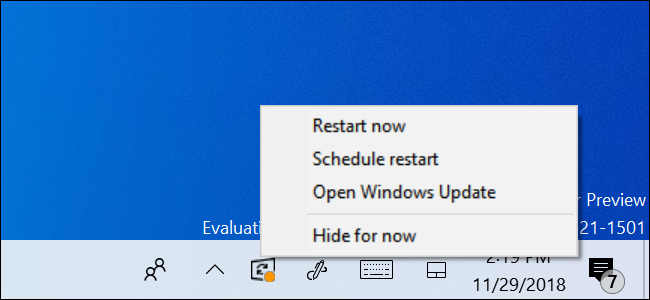
If the Restart now and Schedule restart options do not appear on the icon’s context menu, the message you received earlier was likely fake.
This could mean that malware has already been installed on your system. If you make the unfortunate mistake of restarting your computer, you may find yourself locked out. This is the typical pathology of a ransomware attack.
Other Signs and Symptoms
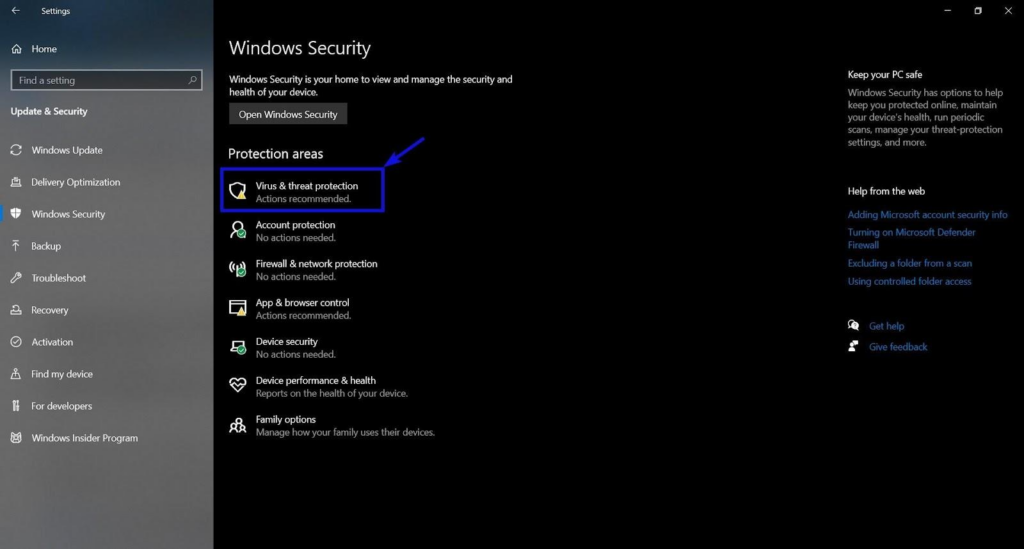
If you don’t have a third-party antivirus or security system installed, make sure your Windows Security Virus and Threat protection settings have not been disabled and blocked.
Pay attention to your network traffic, too. You can use a third-party network monitor, firewall, or Windows Task Manager to find any suspicious apps that may be making unauthorized uploads or downloads:
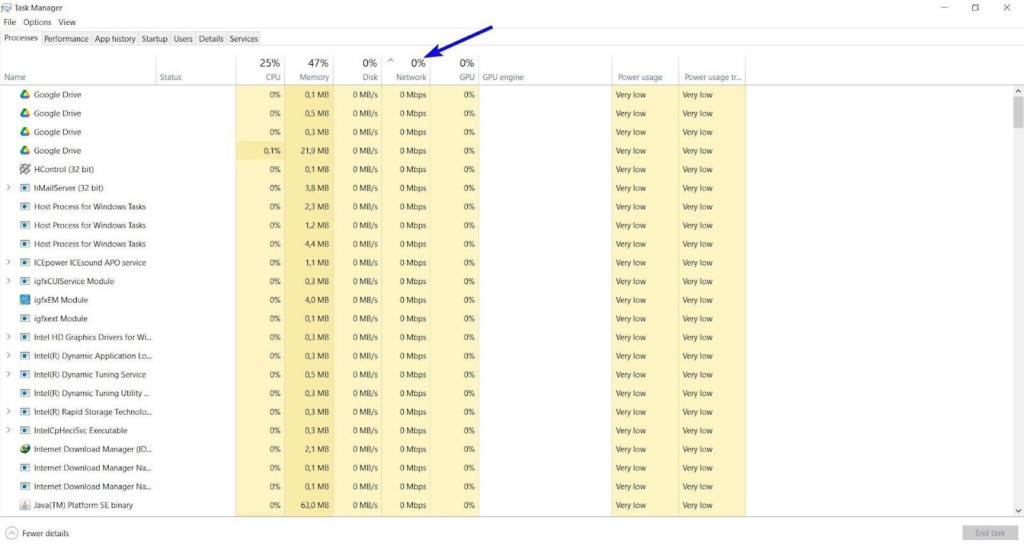
Essentially, this allows you to identify malware or spyware and remove it promptly. However, it’s important to note that this can depend on a lot of factors, such as the quality of your internet security system and how elaborate the threat really is.
Look out for any out-of-the-ordinary system behaviors on your computer. While said behavior may not be the result of a malware infection, it can be a sign of other, non-malware-related, hardware and software issues.
If you notice that you suddenly can’t access certain programs and system settings, the likelihood of your computer being compromised is very high. But what exactly should you do in this case?
Fake Software Updates for Windows OS
It is worth noting that cybercriminals frequently create fake updates for Windows-compatible software, particularly for popular browsers like Google Chrome, which has the largest market share.
To illustrate this tactic, we can safely analyze a phishing website that replicates the design of Google’s official website, specifically the pages for downloading Google Chrome, using the ANY.RUN sandbox.
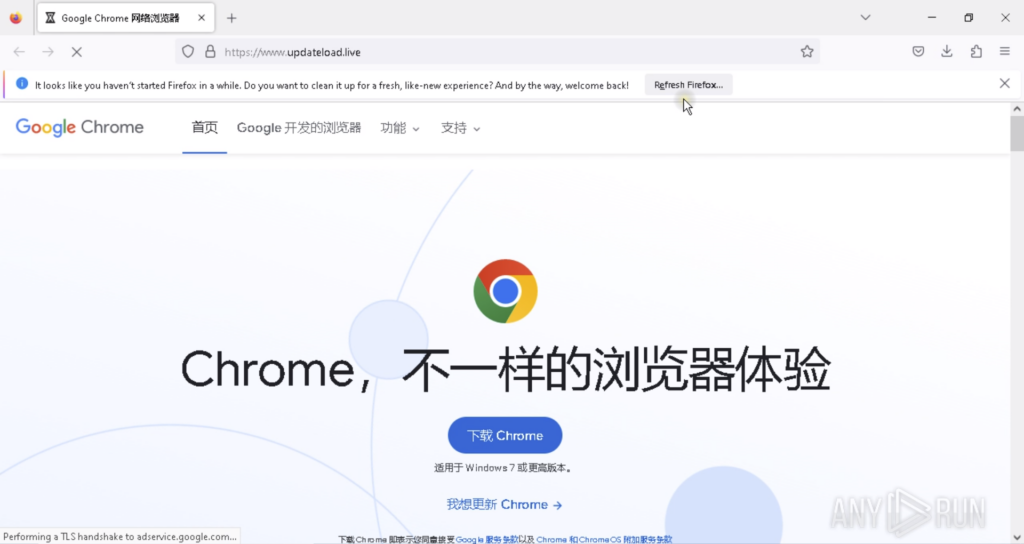
When a user attempts to download the browser from this fake website, they receive an archive named “GoogleUpdate” containing an executable file with the same name. Launching this file installs Cobalt Strike, a program used for penetrating endpoints’ security systems and further delivery of additional malicious payloads.
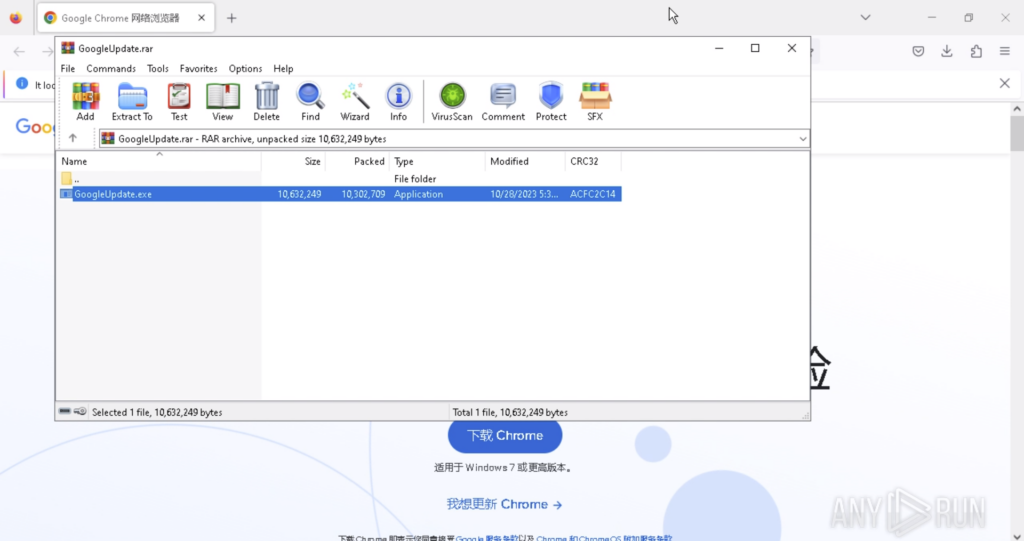
This example clearly demonstrates how cybercriminals can exploit users’ trust in popular software by creating websites that closely resemble the legitimate ones. To protect against these threats, it is crucial to analyze any suspicious link or file before clicking or running it.
This is where ANY.RUN’s comprehensive and fast cloud-based analysis proves valuable, enabling you to quickly determine whether a file or link is malicious and gather IOCs.
Preventative Security Measures
As the old cliche goes: “prevention is better than cure”. Fake Windows updates rely on human error more than they do on system exploits. Thus, there are certain habits you should consider adopting as a part of your cyber-hygiene regimen.
Controlling and Managing Updates
Modern Windows updates are downloaded automatically. While beneficial, it may be more secure to control how and when updates are installed.
You can configure when updates are installed using the active hours setting. Alternatively, you can temporarily disable updates using the Pause option under Windows Update settings.
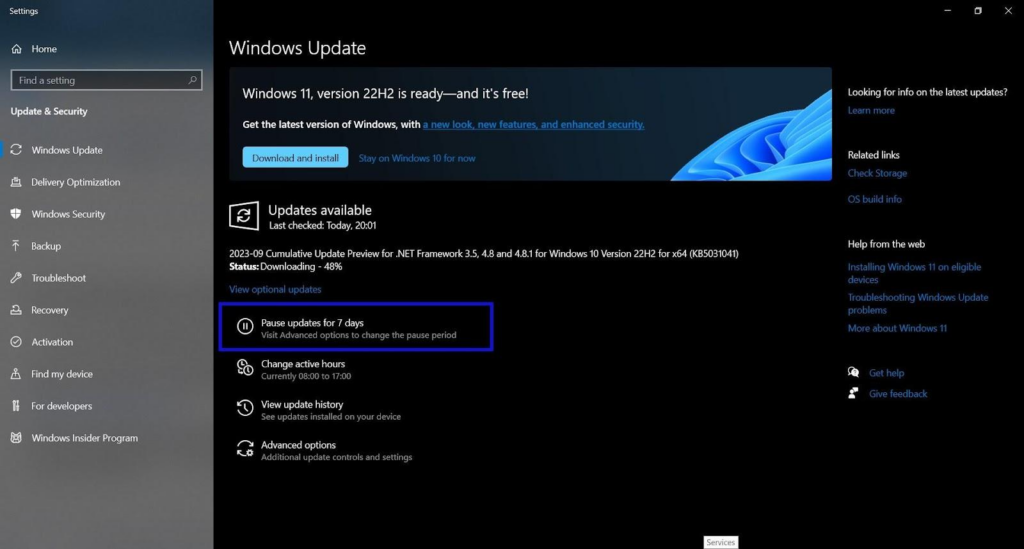
If you want a more permanent solution, you can disable the Windows Update service entirely and rely on sporadic, carefully chosen manual updates:
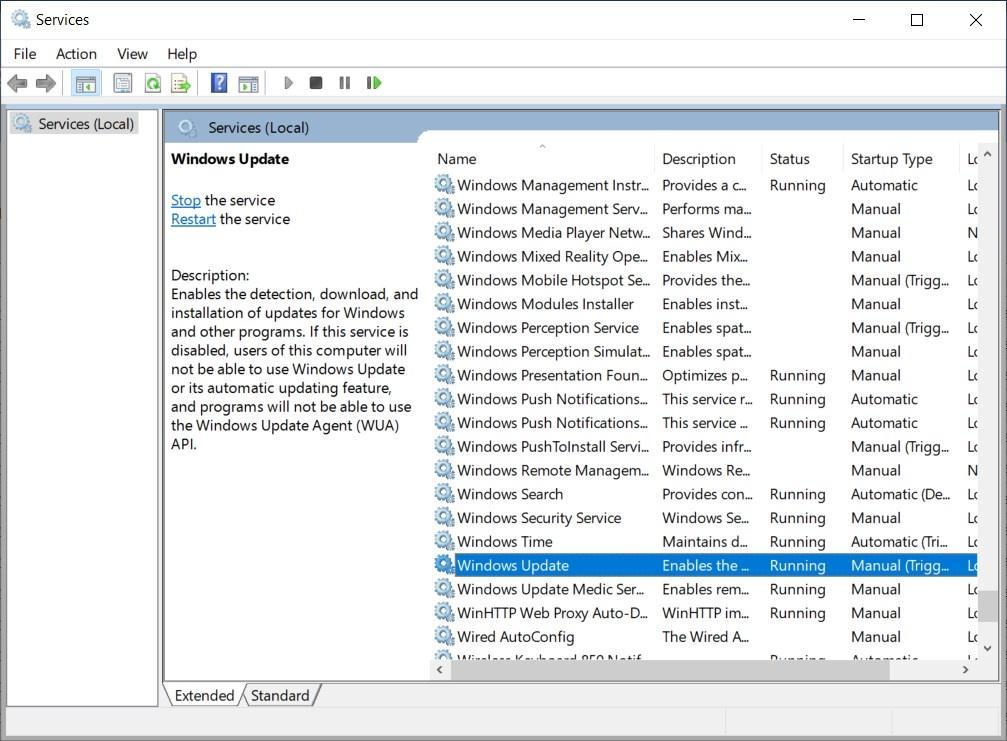
You can then use the Windows Update Catalog website to manually download and install updates for your version of Windows. It’s important that you update Windows or any other software from reliable sources – preferably from the developer or publisher. Nevertheless, knowing how updates function will make it easier for you to identify fake ones.
Perform Regular Backups
You can configure and perform a backup from Windows Update and Security settings.
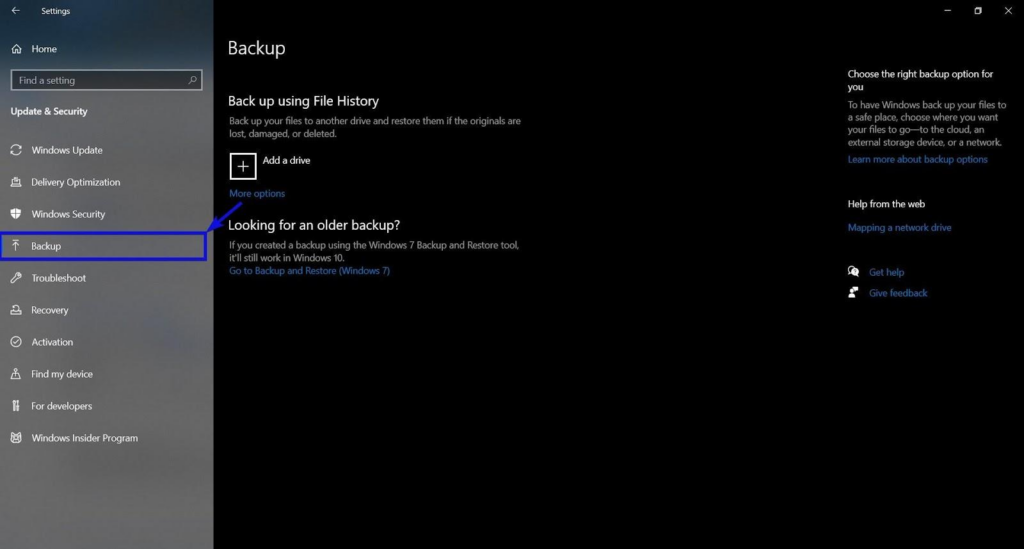
However, you may find it preferable to use a third-party tool. It should be one that can capture an image of your entire hard drive(s). Images are far easier to manage than Windows file backups, as they can be mounted.
Backups should be stored on secure cloud storage or an external hard drive (preferably password-protected). You should also consider creating a rescue/restore/bootup drive, not just a partition, that you can use to restore your backup.
Use Trusted Antivirus and Security Software
Third-party antiviruses and security software tend to have more features and controls than Windows’ default offering.
While All-in-one solutions may be more convenient, it may be safer to control each security point using a different tool. For instance, instead of using an antivirus, you may consider using a dedicated firewall solution to manage your system’s network traffic.
Regardless of which solution you choose, it must be maintained and updated regularly. But what should you do if your security stack fails you and your system suffers a breach?
Dangers and Immediate Response
If your system seems to have been breached in any way, your first step should be to immediately disconnect it from the internet. Modern firewalls allow you to block all incoming and outgoing traffic so you don’t need to physically disconnect yourself from the internet.
Disconnect and Assess
You need to terminate the line of communication from your system to the bad actors. Disconnecting from your network allows you to place your PC into a sandbox. You can then trace the root of the infection and use adequate tools to eradicate it.
Perform a Full System Restore
When dealing with ransomware, you can either give in to the bad actors’ demands or resist. Of course, this will largely depend on how extreme their demands are and if there is a way to circumvent the attack.
If your Windows operating system or the hard drive it lives on has been completely encrypted, you can’t do much to save it. Not even booting into Safe Mode would help.
Thus, your best bet would be to wipe the hard drive (using a boot/rescue disk) and then perform a full system restore using a recent backup. If all else fails, you’ll need to ask a cybersecurity professional for guidance.
Support and Breach Mitigation
If the resultant Fake Windows Update breach becomes company-wide, and your business is US-based, you are required to contact law enforcement as soon as you can. If the cyberattack occurred on your home personal computer, you can still file a complaint with the Internet Crime Complaint Center (IC3). Likewise, companies can also flag incidents through the National Cyber Investigative Joint Task Force.
You can also find helpful resources and information by using the Cybersecurity and Infrastructure Security Agency’s online portal. In addition to having a reliable IT and cybersecurity team, businesses should also consider acquiring a cybersecurity insurance policy. This will help companies minimize losses in the case of a (successful) breach or cyberattack, as well as help you get back on track.
If you somehow survive the cyberattack unscathed and regain control of your system, you need to investigate how the breach occurred. Was it the result of a weak password? Did you download any shady or pirated software? Post-mortems are key for this, and you shouldn’t be lazy with them.
Work on updating your security policies, adding more security controls, monitoring accounts, and changing your passwords. If you’re going to use a password manager, make sure that it’s trusted and secure, too.
Conclusion
Windows updates play a critical role in safeguarding systems. They patch vulnerabilities, improve the user experience and ultimately ensure optimal performance. However, malicious actors use it as a form of social engineering, and a means to infect your PC. Always ensure your updates are coming from Microsoft themselves, and be sure to educate your team about the perils of fake Windows updates.
A few words about ANY.RUN
ANY.RUN is a cloud malware sandbox that handles the heavy lifting of malware analysis for SOC and DFIR teams. Every day, 300,000 professionals use our platform to investigate incidents and streamline threat analysis.
Request a demo today and enjoy 14 days of free access to our Enterprise plan.
Isla Sibanda
Isla Sibanda is an ethical hacker and cybersecurity specialist based out of Pretoria. For over twelve years, she's worked as a cybersecurity analyst and penetration testing specialist for several reputable companies - including Standard Bank Group, CipherWave, and Axxess.
See my website.









0 comments