Speed is one of the biggest advantages of the ANY.RUN sandbox. You can often recognize that a file is potentially malicious in under 20 seconds — whether it’s through the process tree, network stream analysis, or config extraction. Today, we’re adding a new feature to enhance your threat detection: digital signatures. Now, you can easily identify files that have been counterfeited or tampered with.
Digital signatures act like official seals, validating the code’s issuer and signaling to analysts that a file can be trusted. Most large companies use them, signing every file. Kept up to date in public databases, signatures provide robust authenticity checks.
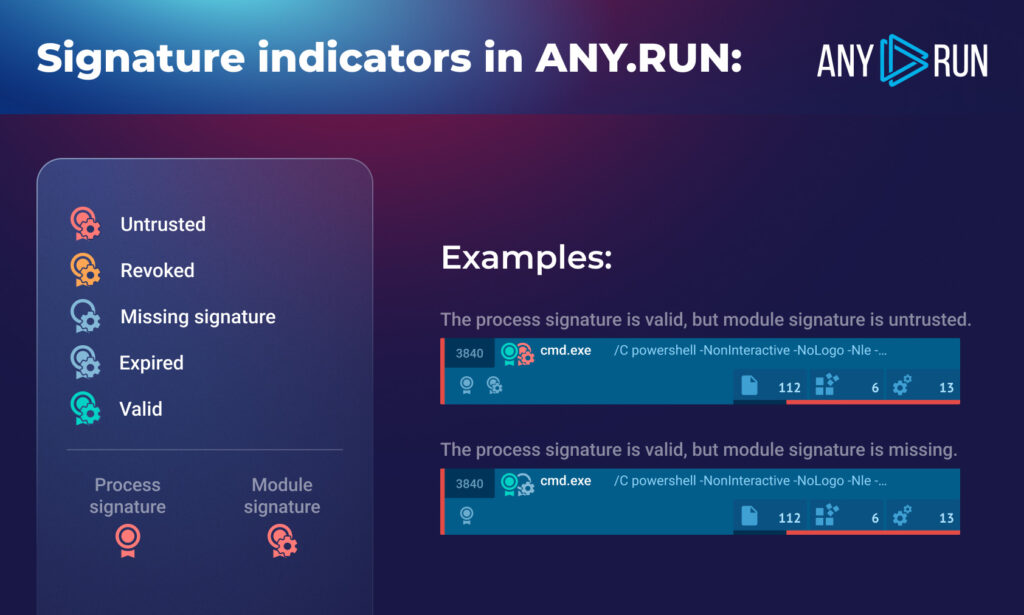
In ANY.RUN, you’ll find new digital signature icons next to processes in the process tree. Semi-transparent icons at the bottom indicate that a process or module has a certificate. Bigger icons at the top mark processes that require further investigation. Here’s when we display them:
- When a module certificate is missing, revoked, or untrusted
- When a process certificate is missing, revoked, or untrusted
How new signature icons work in ANY.RUN
Note that we show different icons for process and module signatures. Even if a process has a valid signature, if its module doesn’t have one — it’s a red flag.
A small cog overlay makes it easy to identify a module signature, differentiating it from its process counterpart.
Using these icons, you can quickly:
- Spot malicious software. A red “untrusted” icon means the signature issuer isn’t recognized. And a hollow icon indicates that a signature is missing.
- Identify untrustworthy files. A yellow “revoked” icon appears if the signature’s public key is compromised.
- Track expired signatures. A light-blue icon shows when the signature’s validity has run out.
Want to know more about the signature? Click on the icon and a code signing window will appear.
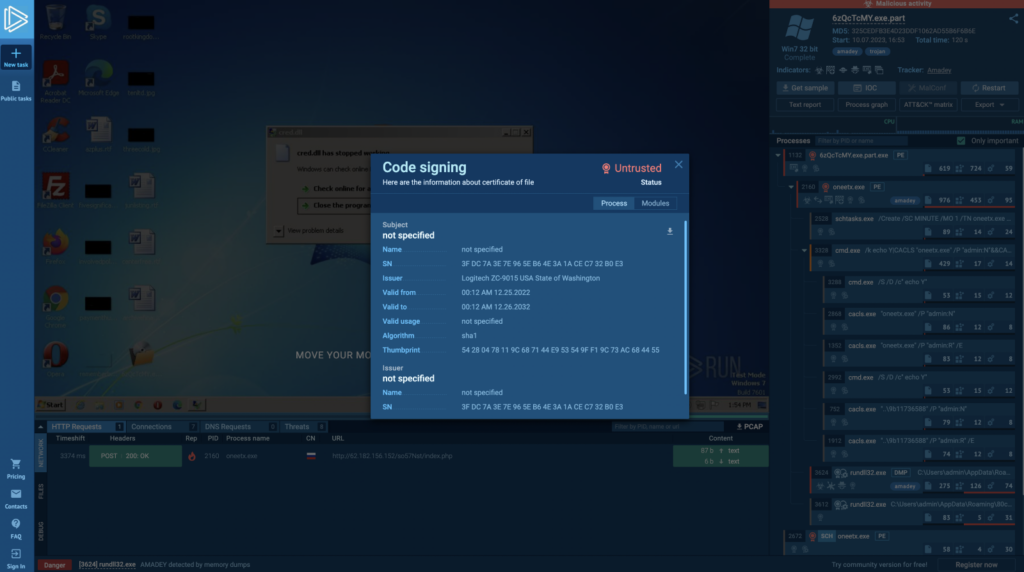
Dive Even Deeper with the ASN.1 Tree
Expired signatures are a dime a dozen in older or end-of-life software. But what if you encounter a suspicious file and want to investigate it further? This is when ASN.1 trees come into the picture. These structured records dive deep into the issuer’s details, revealing who signed the file, when it was signed, and more.
In cases that leave you on the fence, this breakdown can provide the missing piece of the puzzle, enabling you to confidently say if the file is trustworthy.
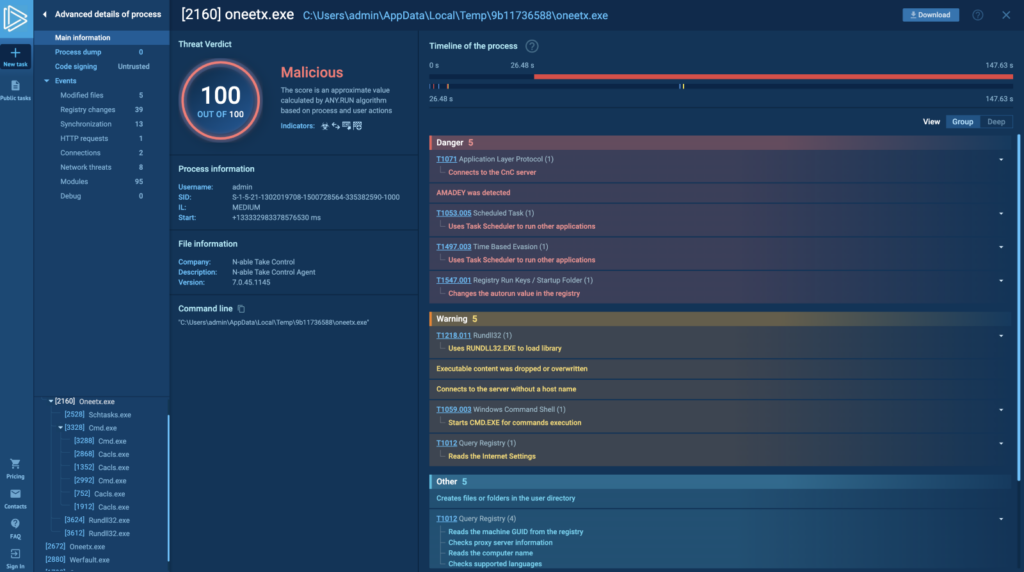
To view the ASN.1 tree, first click on a process and then scroll to the bottom of the process tree, to the process detail window. Then, click the “More info” button. Once the advanced process details page appears, select the new “Code signing” tab. You will see the signature overview on the left side of the window, and the ASN.1 tree will occupy the right side.
From here, you can search the ASN.1 record right in ANY.RUN or download and analyze it further in your system.
Here’s How You Can Use Digital Signatures in the Real-world
Certificates can be one of the first red flags indicating that a sample warrants a closer look.
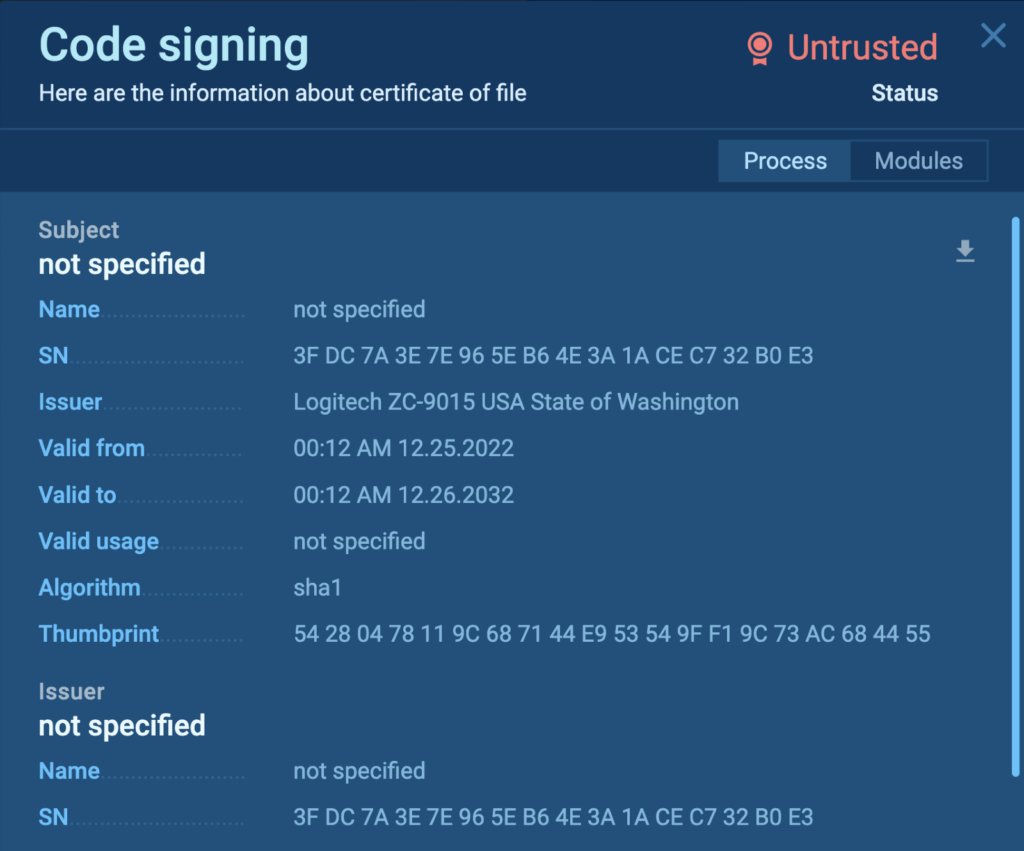
An untrusted status — like in this example — is an obvious indication of malicious code, as the name implies. That is something you will never come across in a legitimate program.
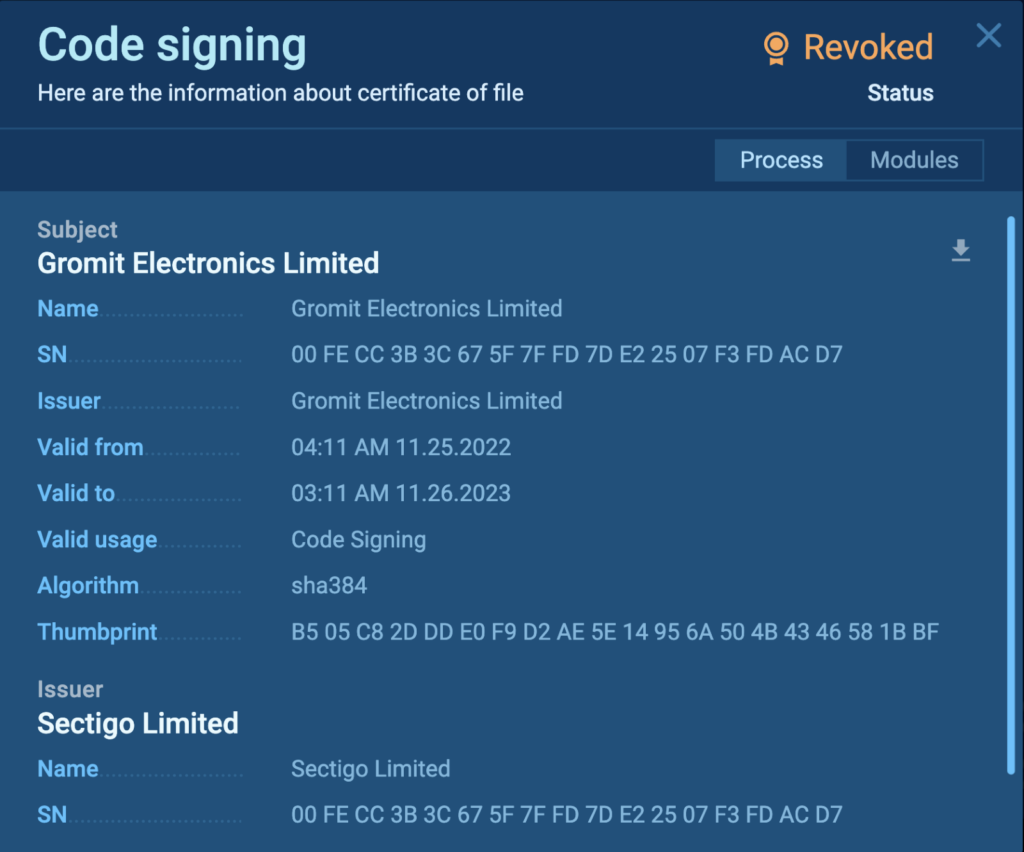
Revoked certificates are similarly unambiguous — this status often indicates that a company has manually called back that certificate. Chances are, they suspect or know that it’s become compromised. That’s exactly what we see in this sample.
And in this task, the certificate is expired. On the surface, this tells us that its validity period has passed and there is foul play, but such cases are still worth a look.
Sometimes attackers steal certificates when they compromise a company. And that is precisely what happened in this task. We’re looking at Agent Tesla, signed with a leaked certificate. Even in a complicated case like this, the system notifies us about a potential certificate irregularity.
Also, there is an icon for valid certificates — it will show up in the process tree if a module signature is missing, indicating a suspicious case.
A few words about ANY.RUN
ANY.RUN is a cloud malware sandbox that handles the heavy lifting of malware analysis for SOC and DFIR teams. Every day, 300,000 professionals use our platform to investigate incidents and streamline threat analysis.
Request a demo today and enjoy 14 days of free access to our enterprise plan.







0 comments