Adversaries today increasingly employ evasive techniques to bypass automated detection and slow down investigation: multi-stage payloads, browser-based phishing flows, CAPTCHA challenges, rewritten URLs, ZIP archives with malicious executables, QR codes, and more.
This is where automated malware analysis becomes essential — enabling security teams to process threats at scale while maintaining the depth of insight needed for accurate detection and response.
What Is Automated Malware Analysis?
Automated malware analysis is the process of using specialized software to automatically examine suspicious files, programs, or URLs for malicious behavior.
This involves utilizing the isolated environment of a malware sandbox to observe actions such as modifying files, connecting to unknown servers, or exploiting vulnerabilities, without risking real systems. It helps security teams quickly identify, classify, and respond to threats at scale, reducing the need for manual analysis.
ANY.RUN’s Sandbox provides automated analysis of suspicious files and URLs via the Automated Interactivity (ML) feature. For security teams, it:
- Eliminates manual work, freeing analysts to focus on high-impact incidents instead of repetitive threat analysis.
- Accelerates threat detection and response, providing rapid verdicts and actionable reports for decisive action to mitigate risks faster.
- Increases a SOC’s capabilities to process alerts, allowing the team to deal with larger volumes of potential risks.
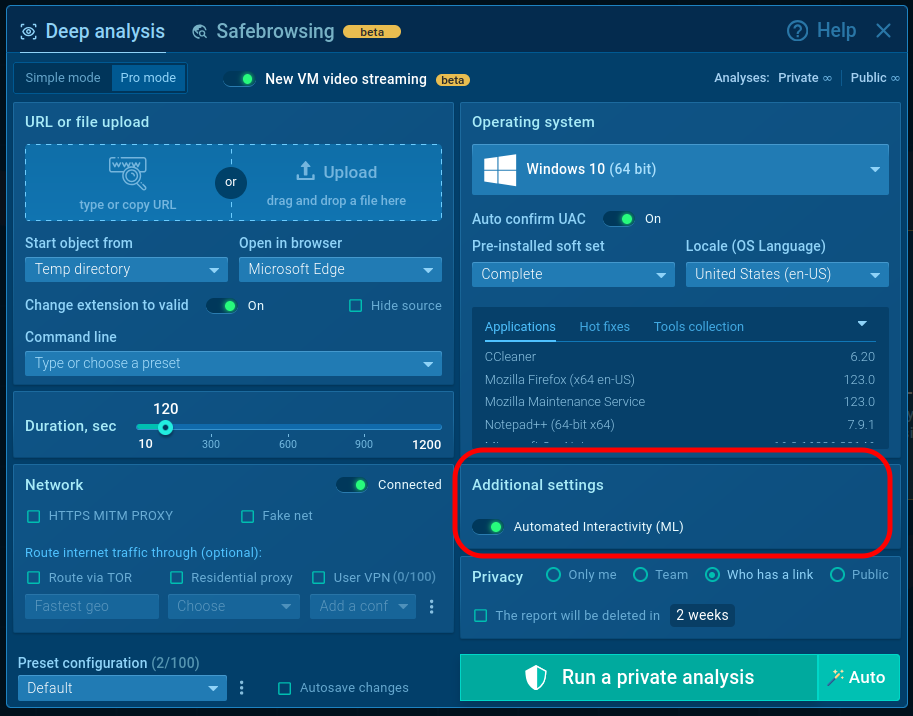
The feature comes with the Enterprise plan and can be enabled in the New analysis window.
For analyses launched via API, it is used by default.
What Automated Malware Analysis Can Do
Automated malware analysis covers a wide range of capabilities that allow threat-analysis systems to execute, observe, and derive actionable intelligence from malware and phishing threats. For example, ANY.RUN’s Automated Interactivity’s key attributes include:
- Automatically launching submitted samples (files, URLs, archives, email attachments) and forcing them through all required steps (e.g., user clicks, CAPTCHA resolution, archive extraction) to reveal their behavior.
- Integrating simulation of human-interactions (auto-clicks, form entries, navigation) so that sandboxed sessions can trigger payloads or flows that are otherwise blocked or stalled by evasion. For example, many phishing sites require CAPTCHAs or button clicks; many installers have sequences of “Next/OK” dialogs. Automation handles those.
- Smart content analysis: the ability to inspect a submitted sample, identify embedded or rewritten content (URLs in QR codes, archive-embedded executables, multi-stage redirects, attachment payloads), extract and detonate them automatically.
In other words, automated malware analysis is an evolution beyond static analysis, standard sandboxing or purely manual interactive sessions: it blends the interactive sandbox with automation and human-behavior simulation to achieve faster, broader, more reliable threat insight.
How Automated Malware Analysis Helps SOCs and MSSPs
For security operations centers and managed security service providers, automated malware analysis fundamentally changes operational metrics and capabilities:
- Reduced Mean Time to Detect (MTTD) and Respond (MTTR): Automated analysis eliminates the delays inherent in manual triage, cutting MTTR by 21 minutes per incident and reducing MTTD to a median 15 seconds.
- Increased Threat Detection Rate: Automated analysis significantly improves detection rates (up to 36% better than traditional security tools) by forcing malware execution and bypassing evasion tactics that would normally cause samples to remain dormant.
- Enhanced Analyst Productivity: By handling repetitive tasks like sample execution, interaction simulation, and initial triage, automation frees analysts to focus on high-value activities such as threat hunting, incident investigation, and strategic security improvements. Teams report productivity increases of up to 3x when implementing automated analysis workflows.
- Improved Alert Quality: Automated analysis reduces false positives by providing comprehensive behavioral data and accurate verdicts. Instead of alerting on every suspicious indicator, security teams receive enriched intelligence about confirmed threats, reducing alert fatigue and improving response prioritization.
- Scalability Without Resource Expansion: MSSPs serving multiple clients can handle increasing sample volumes without proportionally expanding their analyst teams. Automated analysis processes hundreds or thousands of samples daily through API integration, providing consistent analysis depth across all clients.
From a business perspective, automated malware analysis delivers:
- Cost Optimization: Reduced analyst hours per incident translates to lower operational costs and better resource allocation.
- Business continuity and reputation: Faster response and better detection reduce business risk, downtime, regulatory exposure and client dissatisfaction.
- Risk Reduction: Faster threat detection and response minimizes dwell time and reduces the potential impact of security incidents.
- Service Quality: For MSSPs, automation enables consistent analysis quality across all clients, improving service delivery and customer satisfaction.
- ROI on tooling: Automating sandbox interactions and integrating them into broader SOC tooling (SIEM, SOAR, EDR) increases the value derived from sandbox investments.
Automated malware analysis empowers SOCs and MSSPs to scale, speed up and strengthen their threat-analysis workflows while aligning with business objectives of cost-efficiency, risk reduction and improved service delivery.
Using Automated Malware Analysis: Real World Examples
Let’s look at a few real-world examples of using Automated Interactivity.
1. Extracting URL from QR and Solving a CAPTCHA
Let’s view an example of a multi-stage phishing attack analysis.
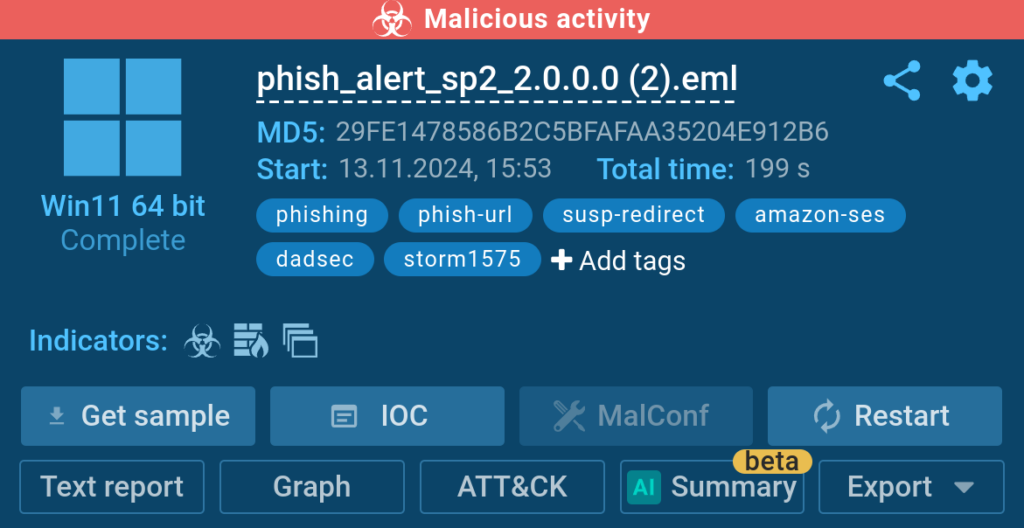
The attack starts with an email:
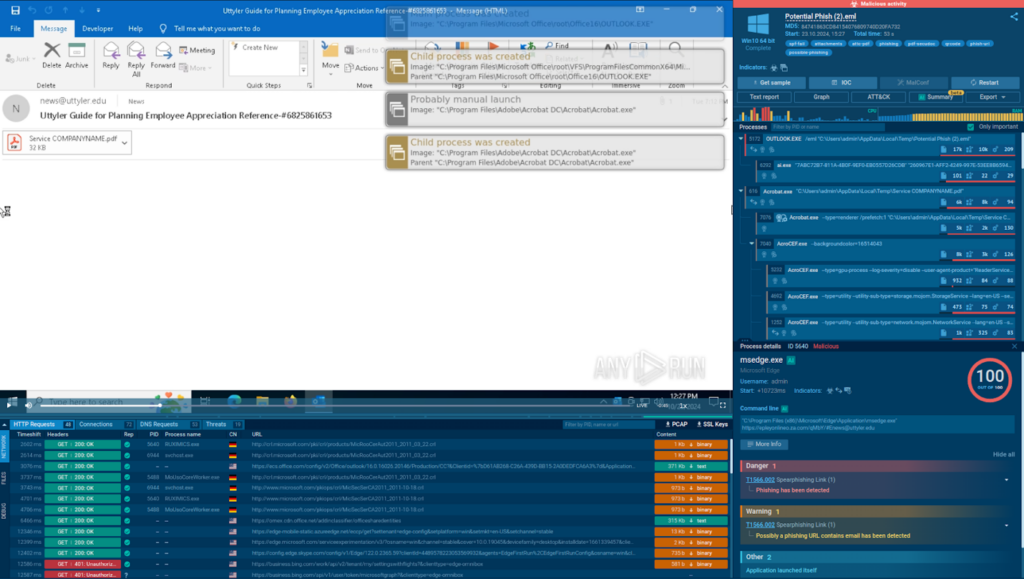
Step 1: We upload the email file to the ANY.RUN sandbox, switch on Automated Interactivity, and start analysis.
Step 2: Automated Interactivity launches the .eml file via Outlook, identifies a PDF attachment, and opens it.
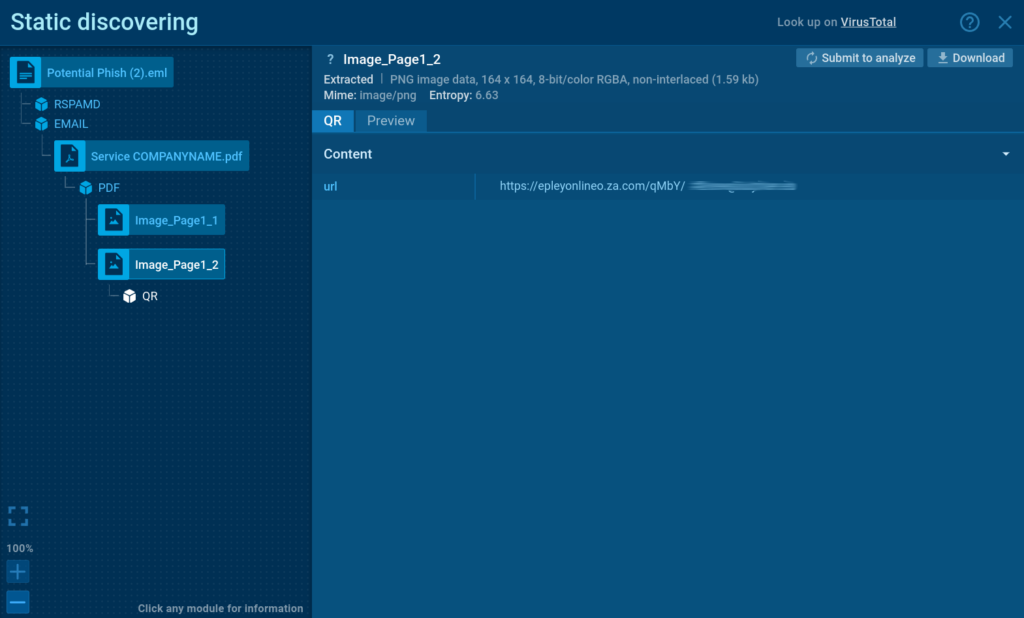
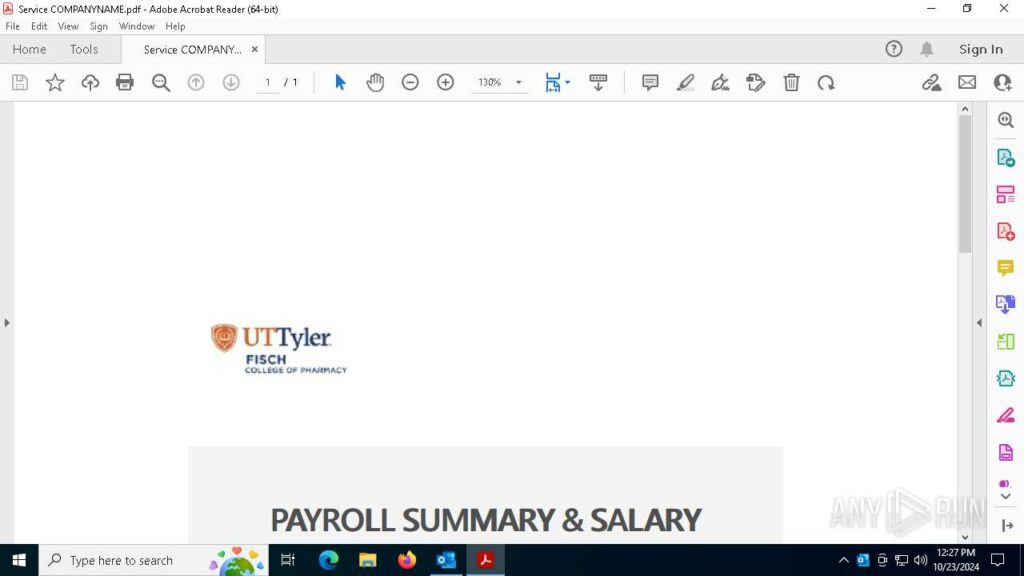
Step 3: After scanning the PDF, it detects a QR code, automatically extracts its embedded URL, and opens it inside a browser.
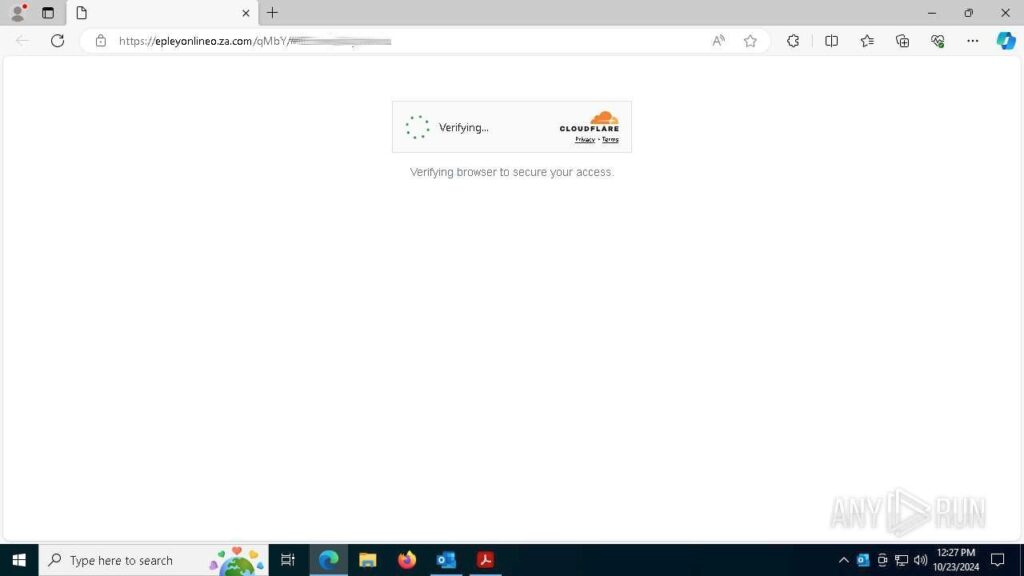
Step 4: The opened page has a CAPTCHA challenge, a common method for evading detection. The sandbox successfully solves the CAPTCHA and proceeds to the next stage.
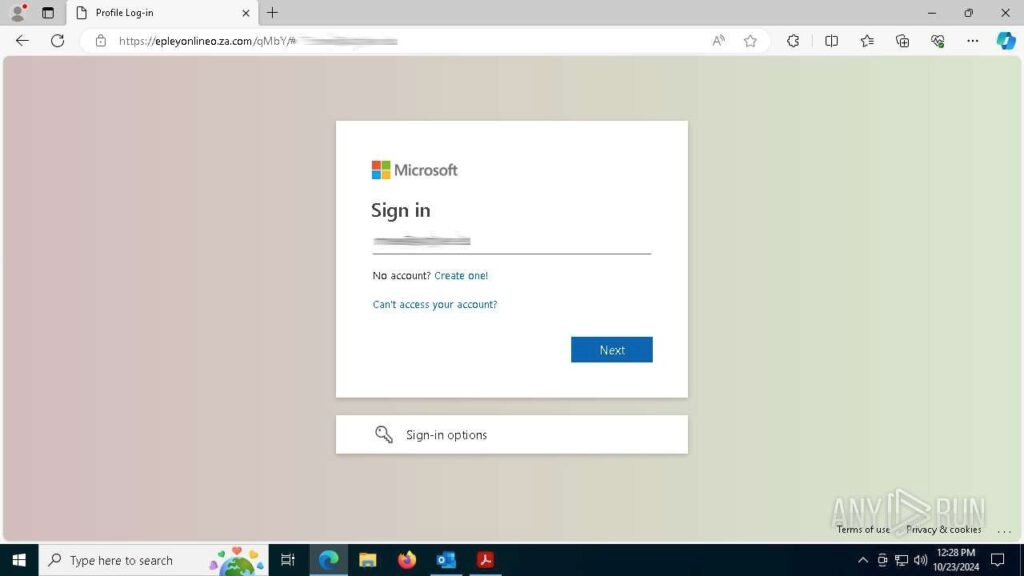
Step 5: Once the final phishing page is loaded, the sandbox instantly assigns the “phish-url” tag to the session and marks it with the “malicious activity” label.
Phishing sites are increasingly adopting methods to evade automated security measures. One prevalent technique involves integrating CAPTCHAs, making them more challenging to block automatically.
2. Analyzing installers
Malware authors frequently embed malware in legitimate software downloaded from the Web, deceiving users into inadvertently installing it. Installers typically demand user interaction, necessitating clicks on buttons like ‘OK’ and ‘Next’. This is how ANY.RUN automates it:
View this sandbox analysis for reference
3. Extracting Rewritten URL
Modern email systems are equipped with spam filtering. While it protects users against threats, it complicates the work of security analysts by blocking their access to the actual malicious content that they wish to examine.
Automated Interactivity bypasses such filters and quickly reaches the resources controlled by the threat actors, saving analysts’ time.
Here is a sandbox session featuring a blocked phishing URL.
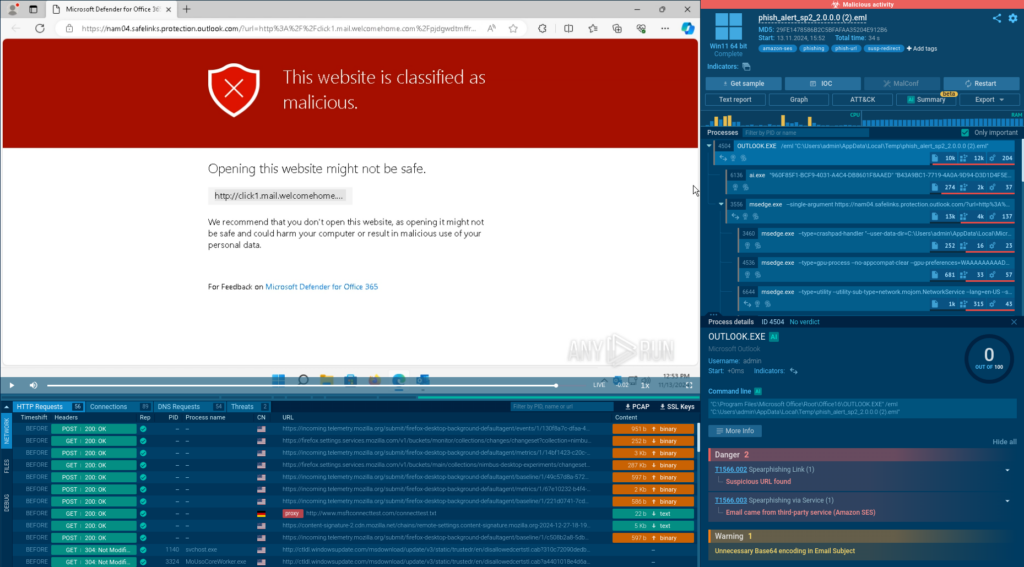
The phishing link inside the analyzed email is rewritten to Microsoft’s domain safelinks[.]protection[.]outlook[.]com and now contains a warning.
While it indicates that the link is malicious, it prevents us from learning more about the threat we’re facing.
To go beyond the block, we can enable Automated Interactivity and rerun the analysis.
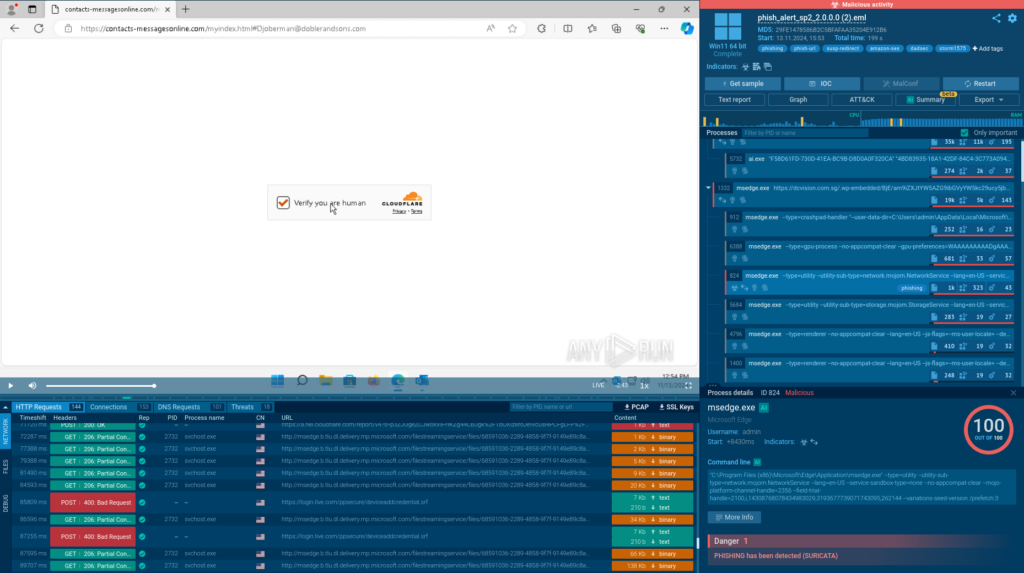
In the rerun sandbox session, the rewritten URL is skipped, and all the stages of the attack, including those requiring solving a CAPTCHA, are detonated automatically. This allows us to go further and discover that the attack is carried out by the Storm-1575 threat actor using the DadSec phishing platform, as shown by the corresponding tags.
ANY.RUN’s Interactive Sandbox supercharges SOC automation by blending detonation with proactive engagement, slashing analysis times for even the most evasive threats — like multi-stage phishing or interaction-dependent malware. Unlike static sandboxes that stall on user prompts, ANY.RUN’s interactivity ensures samples “run wild” under simulated conditions, revealing payloads hidden behind CAPTCHAs, QR codes, or archive layers. For instance, it can autonomously launch an email attachment, scan a PDF for embedded links, solve a Cloudflare challenge, and tag the final phish URL as “malicious activity” in under a minute.
You can get a 14-day trial of ANY.RUN’s Interactive Sandbox to try Automated Interactivity along with other PRO features like private and teamwork mode, as well as integration via API and SDK.
Integrate Automated Malware Analysis in Your SOC
Integrating automated malware analysis via ANY.RUN’s Sandbox is a low-friction process that yields immediate gains. Start by signing up for an Enterprise trial, then:
- API Setup: Generate keys from the dashboard and configure endpoints in your SOAR/SIEM (e.g., POST /tasks/create with sample hashes or URLs).
- Workflow Mapping: Route high-fidelity alerts to the sandbox for auto-detonation; parse JSON responses for auto-tagging (e.g., “malicious” with IOCs).
- Testing and Scaling: Run pilot sessions on historical samples, monitor via dashboard analytics, and expand to full ingestion.
For analysts, benefits are profound: reduced grunt work means more time for high-value tasks like attribution or playbook refinement, cutting burnout and skill gaps — junior team members ramp up 2x faster with guided automations. It democratizes expertise, turning novices into effective hunters.
Business-wise, it aligns with objectives like cost optimization (slash sandbox licensing/maintenance by 30-50%) and revenue growth for MSSPs (offer premium automated services). Faster MTTR minimizes breach dwell time, slashing potential fines under GDPR/NIST, while scalable insights enhance client retention. Ultimately, it drives a proactive security culture, boosting metrics like threat coverage and operational resilience.
About ANY.RUN
ANY.RUN helps more than 500,000 cybersecurity professionals worldwide. Our Interactive Sandbox simplifies malware analysis of threats that target both Windows, Linux, and Android systems. Our threat intelligence products, Threat Intelligence Lookup, YARA Search and Feeds, help you learn more about the threats, gather IOCs, and respond to incidents faster.
Frequently Asked Questions
Traditional sandboxes simply execute files and observe behavior passively. Automated malware analysis actively interacts with samples clicking buttons, solving CAPTCHAs, following links, and extracting content, to force malware execution and bypass evasion techniques. This results in significantly higher detection rates, especially for threats designed to evade automated security tools.
Sessions run in isolated VMs with no outbound access beyond controlled C2 logging, and all data is encrypted with collaboration features for team sharing.
Automated Interactivity addresses multiple evasion categories: user interaction requirements (button clicks, form completion), CAPTCHA challenges (solving via machine learning), environmental checks (realistic VM environment), multi-stage attacks (content extraction and progressive execution), and anti-analysis techniques (human-like behavior simulation). The system continuously evolves as new evasion methods emerge.
Automated analysis with intelligent interactivity achieves detection rates up to 36% higher than traditional automated tools and approaches manual analysis accuracy for most common threat types. For complex, novel threats, automated analysis provides initial triage and behavioral data that enables analysts to complete investigation more efficiently.
Most analyses complete within 60-120 seconds, depending on sample complexity. Simple files execute immediately, while multi-stage attacks requiring multiple interactions may take several minutes. However, because the process is fully automated, analysts can submit dozens of samples simultaneously and review results as they complete.
Yes. ANY.RUN provides comprehensive API and SDK support for integration with SOAR platforms, SIEM systems, EDR solutions, email security gateways, and threat intelligence platforms. The API enables automated submission of suspicious samples, retrieval of analysis results, and extraction of IOCs for automated response workflows.
Automated analysis excels at phishing investigation. The system can analyze email files (.eml, .msg), extract and follow links, scan QR codes, bypass CAPTCHA challenges, follow redirect chains, and reach final credential harvesting pages. It provides complete visibility into phishing infrastructure and tactics.
For samples requiring unusual interactions beyond current automation capabilities, analysts can take manual control within the interactive sandbox. The system provides real-time access to the virtual environment, allowing analysts to complete any actions needed while maintaining full behavioral monitoring and recording.
When automated analysis encounters password-protected archives, the system attempts common passwords and patterns. For phishing emails where passwords are included in the email body (a common attacker technique), Smart Content Analysis can extract the password and apply it automatically. For other cases, analysts may need to provide passwords manually.
Absolutely. Automated analysis is especially valuable for smaller teams because it extends their capabilities without requiring deep malware analysis expertise. The system provides clear verdicts, extracted IOCs, and comprehensive reports that enable even junior analysts to make informed response decisions. This levels the playing field against well-resourced threat actors.







0 comments